The impact of Big Data on the Android Mobile Platform for Natural Disaster Situations
Volume 3, Issue 2, Page No 206–210, 2018
Adv. Sci. Technol. Eng. Syst. J. 3(2), 206–210 (2018);
 DOI: 10.25046/aj030224
DOI: 10.25046/aj030224
Keywords: Android, OCEMA, Big Data, DWH, Natural Disasters
This application developing for the project OCEMA comes as result of architecture building in Android, then the development of a professional modeling in Talend Open Studio for Big Data, which enabled the integration of data from many data sources. One of its uses is the quick identification of people found in areas affected by natural disasters. The application identifies the persons who do not have an ID card, or another identification document, by using identification through fingerprint or personal number. OCEMA Application has access to all the agencies involved in natural disasters managing, such as ISK, HMIK, MIK, FSK and CRA. This application is developed to connect to web applications as well, such as applications, which gather real time information on earthquakes and weather in the world. The study of literature and the actual work with these systems has shown some important components of success for DWH systems, DataMart and mobile application development.
1. Introduction
In the year 2002 alone, disasters affected a staggering 680 million people worldwide. Natural disasters include bring earthquakes, flooding, droughts, heat waves, cold spells and events that destroy countries, businesses and individual property and well-being.
The goal of this study is to investigate the adoption of cell phones as preparedness efforts during the natural disaster seasons in a developing country. Since Kosovo is a country vulnerable to natural disasters, the present study aims to investigate the adoption of cell phones for natural disaster preparedness [1]
OCEMA applications initially are secured by a username and password, and then divided in 5 buttons, such as: ISK, CRA, HMIK, MIK and FSK. This application enables access to real time information, such as in the case of the agency of civil register, offering two possibilities to identify the victims of natural disasters.
It uses the identification through personal number, but in cases where there is no ID card, the identification can be done using the fingerprints. Part of this application is access to institutions such as the Institution of Seismology, the Medical Institution, the Hydro meteorological Institution and the Firefighter’s Service.
These institutions have updated information. Beside this, the OCEMA application has the possibility to access important web pages in order to monitor climate and seismic conditions in world level.
2. Mobile Platforms
The four most common smart phone operating systems, by market share in the third quarter of 2013 (IDC 2013) are:
- Android by Google, with a distinct dominance at 81 %,
- iOS, on Apple’s iPhone, at 12.9 %,
- Windows Phone by Microsoft at 3.6 %
- and BlackBerry at 1.7 %.
There are many significant differences between these platforms. Some are visible to the users such as availability of specific features or design of the user interface (UI), and some are invisible to the users but affect the developers of mobile applications.
2.1. Android architecture
Starting from the bottom we have Linux Kernel, Android is built up on the Linux Kernel. Linux is already being used extensively from so many years and its kernel had received so many security patches. Linux Kernel provides basic system functionality like process management, memory management, device management like camera, keypad, display etc.
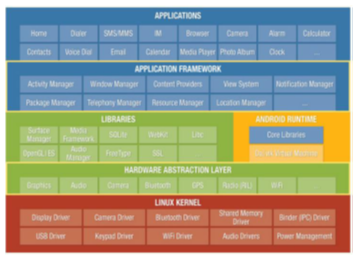 Figure 1: Android Architecture [2]
Figure 1: Android Architecture [2]
As the base for a mobile computing environment, the Linux kernel provides Android with several key security features, including:
- A user-based permissions model
- Process isolation
- Extensible mechanism for secure IPC
- The ability to remove unnecessary and potentially insecure parts of the kernel.
As a multiuser operating system, a fundamental security objective of the Linux kernel is to isolate user resources from one another. The Linux security philosophy is to protect user resources from one another [2]
Taking into consideration the Android as a target platform for application comes as the result of reviewing various works using Android technology.
The Android SDK allows application development with great ease. There are many inbuilt features and tools in an Android device, which can be integrated and programmed to be used as and when required from within the application [3]
3. Case study: SQLite_OCEMA database integration can be implemented in Android mobile devices
The operational Centre of the Emergency Management Agency requires analysis in daily, weekly and monthly bases. What is most important is the capability of real time data analysis. Therefore, this increases the need for data collection and data integration in a single database. The scope is to be able to analyze possible problems faced during emergency situations and natural hazards and then determine the highest levels of entities from which we can collect data.
The following data form the bases of the conceptual model of OCEMA database, which we are going to build.
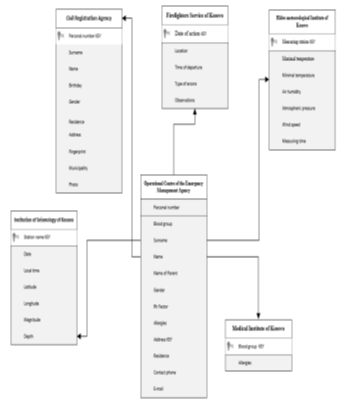 Figure 2: The Entity Relationship diagram of OCEMA database
Figure 2: The Entity Relationship diagram of OCEMA database
We start with the description of the entities used in the OCEMA database.
The entity named Medical Institute of Kosovo is composed of the following data: Blood group for the patients and the eventual allergies present in the population. Entry data from MIK are an important information source at national level as far as the health of the population is concerned.
The entity named Civil Registry Agency includes several fields involving records on entry data regarding the civil registration at a national level, among them including the following characteristics: personal number, surname, name, date of birth, residence, address, fingerprints, district and photo.
All these attributes of the CRA entity include the population’s records. In our study, the principal searching attributes on individuals will be the personal number and the fingerprints.
The entity named Institute of Seismology of Kosovo includes the following attributes: name of the weather station from where we get the real time data on seismic waves and information from the instruments of online monitoring of seismic waves.
Then in this entity we include: the date of seismic waves, local time, latitude, longitude, magnitude and seismic depth.
The data entity generated by the Hydro meteorological Institute of Kosovo includes a very significant dynamics of available data aiming the comprehensive real time monitoring in order to prevent flooding from rainfall, snow and also extreme draught caused by extreme maximal temperatures.
This entity includes the following attributes: the weather measuring station, maximal temperature, minimal temperature, air humidity, atmospheric pressure, wind speed, measuring time.
It is very important to keep under control the continuous monitoring and observation of many factors, which affect arsons, such as the case of arsons involving homes, forests and pastures.
The entity of Firefighters Service is composed of the following attributes: date of action, location, time of departure, type of arsons, observations. All of these offer a very good opportunity to get information from this very important institution.
4. Data integration in SQLite_OCEMA through Talend Open Studio for Big Data
We have chosen SQLite as the main database, where we will integrate the tables from Oracle SQL, such as: CRA, HMIK, MIK, ISK and FSK. Most of the enterprise companies use Oracle in their applications in order to load data. In the case of data loading in SQLite_OCEMA, we have built the following job in Talend Open Studio for Big Data, as shown in the Figure below:
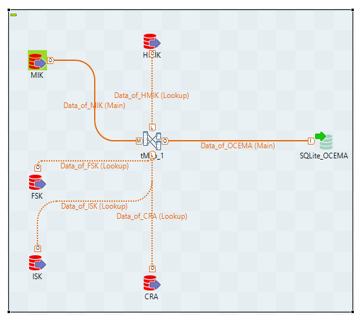 Figure 3: Talend’s Job for data loading from the ORACLE SQL tables in SQLite_OCEMA
Figure 3: Talend’s Job for data loading from the ORACLE SQL tables in SQLite_OCEMA
These heterogeneous data sources, HMIK, MIK, FSK, ISK and CRA, then will be stored in SQLite_OCEMA databases, as shown in the TOS schema.
An important step in ensuring the job developing with ETL is the successful connection between TOS and SQLite_OCEMA database.
4.1. Projecting the SQLite _OCEMA database
Unlike most RDBMS products, SQLite does not have client/server architecture. Most large-scale database systems have a large server package that makes up the database engine.
The database server often consists of multiple processes that work in concert to manage client connection, I/O files, caches, query optimization and query processing. A database instance typically consists of a large number of files organized into one or more directory trees on the server’s file system.
In order to access the database, all the files must be present and correct. This can make it somewhat difficult to move or reliably back up a database instance. To access the database, client software libraries are typically provided by the database vendor. These libraries must be integrated into any client application that wishes to access the database server.
These client libraries provide APIs to find and connect to the database server, as well as set up and execute database queries and commands. The Figure 4 below shows how everything fits together in a typical client/server RDBMS.
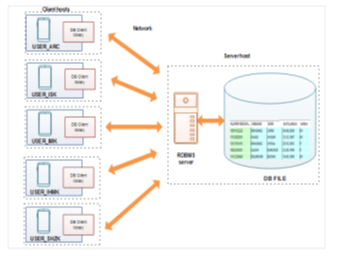 Figure 4: Client/server RDBMS architecture [4]
Figure 4: Client/server RDBMS architecture [4]
In contrast, SQLite does not have a separate server. The entire database engine is integrated into whatever application needs to access a database.
The only shared resource among applications is the single database file as it sits on disk. If we need to move or back up the database, we can simply copy the file. Below, in the Figure 5, we will see the SQLite architecture.
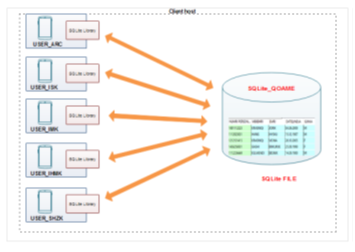 Figure 5: The SQLite server architecture [4]
Figure 5: The SQLite server architecture [4]
By eliminating the server, a significant amount of complexity is removed. This simplifies the software components and nearly eliminates the need for advanced operating support. Unlike a traditional RDBMS server that requires advanced multitasking and high performance inter-process communication, SQLite requires little more than the ability to read and write to some type of storage.SQLite is designed to be integrated directly into an executable. This eliminated the need for an external library and simplifies distribution and installation. Removing external dependencies also removes most versioning issues.
If the SQLite code is built right into the application, we never need to worry about linking to the correct version of a client library or that the client library is version-compatible with the database server. Eliminating the server imposes some restrictions. SQLite is designed to address localize storage needs, such as a web server accessing the local database. This means it isn’t well suited for situations where multiple client machines need to access a centralized database. That situation is more representative of client/server architecture and is better serviced by a database system that uses the same architecture. [4]
4.2. SQLite_OCEMA database-the case of android application for CRA
Android uses the SQLite database system, which is an open-source, stand-alone SQL database, widely used by many popular applications.
SQLite is a lightweight transactional database engine that occupies a small amount of disk storage and memory, thus, it is a perfect choice for creating databases on many mobile operating systems such as Android and iOS [2]
The Android platform offers full support for SQLite databases. The created database will be accessible by name from each of the classes inside the application, not those from outside. In our case, when we are searching the data from the Civil Registration Agency in case of emergencies and natural disasters, we have the possibility to search for missing people during lifesaving operations and also in the warning period of natural hazards.
Thus, we use the personal number identification method to find people struck there where the natural disaster happened. If we take the Civil Registration Agency table of the SQLite_OCEMA database as in the following Table 1:
Table 1: Civil Registration Agency data table in the SQLite_OCEMA database.
5. Searching the SQLite_OCEMA data using the personal number
If we set as criteria the searching of data using the personal number method from the SQLite _OCEMA database and we use the recommended methods to create a new SQLite database.
When a database has been successfully opened, the SQLite Open Helper will cache it, so you can (and should) use these methods each time you query or perform a transaction on the database, rather than caching the open database within your application.
A call to getWritableDatabase can fail due to disk space or permission issues, so it’s good practice to fall back to getReadableDatabase method for database queries if necessary. In most cases this method will provide the same, cached writeable database instance as getWritableDatabase [5]. An example is shown in the Figure 6.
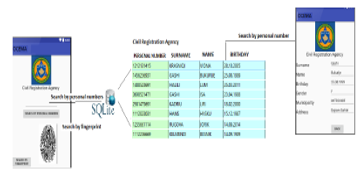 Figure 6: Searching by personal number in SQLite_OCEMA database [6]
Figure 6: Searching by personal number in SQLite_OCEMA database [6]
This is a part of the application development. In this part, we search for people struck by natural disasters and emergency situations by using the fingerprint method, as shown in the Figure.
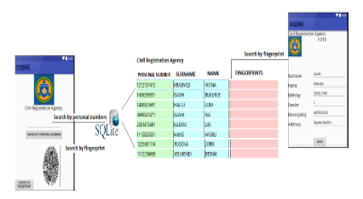 Figure 7: Searching by using the fingerprints in SQLite_OCEMA database.[6]
Figure 7: Searching by using the fingerprints in SQLite_OCEMA database.[6]
This result is displayed every time the user launches the matching activity from our proposed application, by comparing the initial fingerprint with the ones stored in database.
One utility of the proposed application consists in quick identification of the people struck in areas hit by natural hazards or emergency operations, in the quick identification of those people who do not have an ID card or another document of identification, by using the fingerprints identification method. Also, the application could be deployed in the access systems of the public institutions like schools, libraries, hospitals and so on[7]
6. SQLite_OCEMA database- the case of android application for ISK
The Institution of Seismology has a large number of weather measuring stations across the territory of Kosovo. These stations transmit their data to the institute on daily, weekly and monthly bases. Upon creating and building the SQLite_OCEMA database, these data can be reported in a shorter time, better to say in real time across all the weather measuring stations.
By clicking on the ISK (Institute of Seismology of Kosovo) button in the OCEMA basic application, we gain access to search the latest updated ISK data, as shown below in the Figure 8.
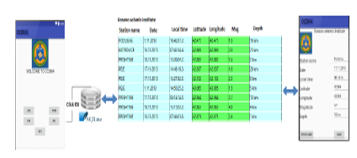 Figure 8: Access to the data of Institute of Seismology of Kosovo. [6]
Figure 8: Access to the data of Institute of Seismology of Kosovo. [6]
After the creation of the Institution of Seismology of Kosovo table in the SQLite_OCEMA database, we can click on the ISK button to search the latest updated data of this institution, including magnitude of seismic waves, seismic depth, geographical position, latitude-longitude, date and time of the seismic wave.
7. SQLite_OCEMA database, the case of Android application for HMIK
The Hydro meteorological Institute of Kosovo has a large number of weather measuring stations across the territory of Kosovo. These stations transmit their data to the institute on daily, weekly and monthly bases. Upon creating and building the SQLite_OCEMA database, these data can be reported in a shorter time, better to say in real time across all the stations, including data from the river flows, data from sensors placed in locations where there is more snow.
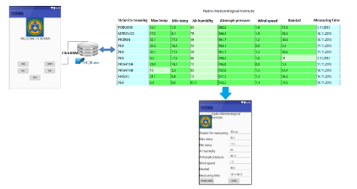 Figure 9: Data from SQLite database for the HMIK case [6]
Figure 9: Data from SQLite database for the HMIK case [6]
Thanks to this application we have been able to get detailed information from all the weather measuring stations in the territory of Kosovo, which provide a representation of warnings in case of flooding from atmospheric precipitations, wind speed, air humidity and the maximum and minimum temperatures.
8. Conclusion
Mobile technology has shown a considerable impact on society over the past few years. Gradually, this technology has become part of every person’s life and is the easiest mode to deliver information. The development of application OCEMA for the doctoral project comes as a result of building architecture in Android Platform, then a professional model in Talend Open Studio for Big Data, which enabled the data integration from multiple data sources. Then we have developed the applications in Android Platform using the Java programming language. We have made it possible to reach near real time representation of the sources.
It is widely known that during natural disasters and emergencies, we do not have all the information available, but in those moments, everything is important, above all the information related to the human factor. EMA should be aware of these kinds of situations and precede the capacity building in systems communication and developing applications for the management of emergencies and natural disasters.
- Lawson, L.Willoughby, “Adoption of cell phones as preparedness efforts for natural disasters”, Issues in Information Systems, International Association for Computer Information Systems, USA, 2012, Vol. 13, pp 11-20 http://iacis.org/iis/2012/79_iis_2012_11-20.pdf
- Agrawal “Android Application Security Part 2-Understanding Android Operating System”, 2015, http://manifestsecurity.com/android-application-security-part-2
- Tejassvi, “An Android application to support flash flood disaster response management in India” M.sc Thesis, University of Twente -Netherlands, 2014.
- Kreibich, Using SQLite, Published by O’Reilly Media, 2010, USA.
- Meier, Professional Android™ 4 Application Development, John Wiley & Sons, Inc., 2012, Canada.
- EMERGENCY MANAGEMENT AGENCY-logo (2015) https://ame.rks-gov.net/en/Home/PgrID/494/PageID/4.
- Dospinescu,I. Lîsîi ,“The Recognition of Fingerprints on Mobile Applications – an Android Case Study” , IBIMA Publishing , Romania,2016 http://ibimapublishing.com/journals/JEERBE/2016/813264/813264.html
- Dharmender Salian, Steven Brown, Raed Sbeit, "Digitalization Review for American SMEs", Advances in Science, Technology and Engineering Systems Journal, vol. 9, no. 4, pp. 93–101, 2024. doi: 10.25046/aj090410
- Marcos Felipe, Haiping Xu, "HistoChain: Improving Consortium Blockchain Scalability using Historical Blockchains", Advances in Science, Technology and Engineering Systems Journal, vol. 8, no. 3, pp. 89–99, 2023. doi: 10.25046/aj080311
- Fatima-Zahra Elbouni, Aziza EL Ouaazizi, "Birds Images Prediction with Watson Visual Recognition Services from IBM-Cloud and Conventional Neural Network", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 6, pp. 181–188, 2022. doi: 10.25046/aj070619
- Mohammad Shadeed, Layth Abu Arram, Majdi Owda, "Forensic Analysis of “WhatsApp” Artifacts in Android without Root", Advances in Science, Technology and Engineering Systems Journal, vol. 7, no. 2, pp. 127–132, 2022. doi: 10.25046/aj070212
- Osaretin Eboya, Julia Binti Juremi, "iDRP Framework: An Intelligent Malware Exploration Framework for Big Data and Internet of Things (IoT) Ecosystem", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 5, pp. 185–202, 2021. doi: 10.25046/aj060521
- Jean Gane Sarr, Aliou Boly, Ndiouma Bame, "Data Stream Summary in Big Data Context: Challenges and Opportunities", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 4, pp. 414–430, 2021. doi: 10.25046/aj060447
- Carla Blank, Matthew McBurney, Maria Morgan, Raed Seetan, "A Survey of Big Data Techniques for Extracting Information from Social Media Data", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 3, pp. 189–204, 2021. doi: 10.25046/aj060322
- Khadija Alaoui, Mohamed Bahaj, "Categorization of RDF Data Management Systems", Advances in Science, Technology and Engineering Systems Journal, vol. 6, no. 2, pp. 221–233, 2021. doi: 10.25046/aj060225
- Safae Bourhnane, Mohamed Riduan Abid, Khalid Zine-Dine, Najib Elkamoun, Driss Benhaddou, "High-Performance Computing: A Cost Effective and Energy Efficient Approach", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1598–1608, 2020. doi: 10.25046/aj0506191
- Sara Ftaimi, Tomader Mazri, "Handling Priority Data in Smart Transportation System by using Support Vector Machine Algorithm", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1422–1427, 2020. doi: 10.25046/aj0506172
- Alexi Delgado, Enrique Lee Huamaní, Alfredo Chiara-Sotomayor, Florencio Roman-Casahuamán, "Design of a Mobile Application for the School Enrollment Process in Order to Prevent Covid-19", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 1042–1046, 2020. doi: 10.25046/aj0506126
- Majdouline Meddad, Chouaib Moujahdi, Mounia Mikram, Mohammed Rziza, "Optimization of Multi-user Face Identification Systems in Big Data Environments", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 762–767, 2020. doi: 10.25046/aj050691
- Alexander Raikov, "Accelerating Decision-Making in Transport Emergency with Artificial Intelligence", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 6, pp. 520–530, 2020. doi: 10.25046/aj050662
- Hana Yousuf, Asma Qassem Al-Hamad, Said Salloum, "An Overview on CryptDb and Word2vec Approaches", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 1282–1287, 2020. doi: 10.25046/aj0505154
- Safaa Alwajidi, Li Yang, "Bayes Classification and Entropy Discretization of Large Datasets using Multi-Resolution Data Aggregation", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 460–468, 2020. doi: 10.25046/aj050557
- Khaldoon Fadhel Brethee, Ghalib Rzayyig Ibrahim, Rashaq Abdullah Mohammed, "Using Envelope Analysis and Compressive Sensing Method for Intelligent Fault Diagnosis of Ball Bearing", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 370–375, 2020. doi: 10.25046/aj050546
- Ladislav Burita, Ales Novak, "ISR Data Processing in Military Operations", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 314–331, 2020. doi: 10.25046/aj050540
- Hana Yousuf, Asma Yousuf Zainal, "Quantitative Approach in Enhancing Decision Making Through Big Data as An Advanced Technology", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 5, pp. 109–116, 2020. doi: 10.25046/aj050515
- Rajesh Kannan Megalingam, Santosh Tantravahi, Hemanth Sai Surya Kumar Tammana, Nagasai Thokala, Hari Sudarshan Rahul Puram, Naveen Samudrala, "ROS Based Multimode Control of Wheeled Robot", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 688–696, 2020. doi: 10.25046/aj050285
- Nuno Martins, Jéssica Campos, Ricardo Simoes, "Activerest: Design of A Graphical Interface for the Remote use of Continuous and Holistic Care Providers", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 635–645, 2020. doi: 10.25046/aj050279
- Shweta Mittal, Om Prakash Sangwan, "Big Data Analytics Using Deep LSTM Networks: A Case Study for Weather Prediction", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 133–137, 2020. doi: 10.25046/aj050217
- Johannes Linden, Xutao Wang, Stefan Forsstrom, Tingting Zhang, "Productify News Article Classification Model with Sagemaker", Advances in Science, Technology and Engineering Systems Journal, vol. 5, no. 2, pp. 13–18, 2020. doi: 10.25046/aj050202
- Allae Erraissi, Abdessamad Belangour, "A Big Data Security Layer Meta-Model Proposition", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 5, pp. 409–418, 2019. doi: 10.25046/aj040553
- Alvina Aulia, Yogi Udjaja, Irma Kartika Wairooy, Adithia Panji Hutama, Dinar Khansa Shabira, Sabilal Muhtadin, "Android Application to Detect Cat Disease Using an Expert System", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 5, pp. 158–162, 2019. doi: 10.25046/aj040521
- Waleed Al Shehri, Maher Khemakhem, Abdullah Basuhail, Fathy E. Eassa, "A Proposed Architecture for Parallel HPC-based Resource Management System for Big Data Applications", Advances in Science, Technology and Engineering Systems Journal, vol. 4, no. 1, pp. 40–44, 2019. doi: 10.25046/aj040105
- Tareq Khan, "A Wi-Fi based Architecture of a Smart Home Controlled by Smartphone and Wall Display IoT Device", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 6, pp. 180–184, 2018. doi: 10.25046/aj030623
- Mohamed Adel Serhani, Hadeel Al Kassabi, Ikbal Taleb, "Towards an Efficient Federated Cloud Service Selection to Support Workflow Big Data Requirements", Advances in Science, Technology and Engineering Systems Journal, vol. 3, no. 5, pp. 235–247, 2018. doi: 10.25046/aj030529
- M. Raihan, Saikat Mondal, Pritam Khan Boni, Arun More, Md. Omar Faruqe Sagor, "Smartphone Based Heart Attack Risk Prediction System with Statistical Analysis and Data Mining Approaches", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 3, pp. 1815–1822, 2017. doi: 10.25046/aj0203221
- D. Siva Sankara Reddy, R. Udaya Kumar, "Big Data Analytics for Healthcare Organization: A Study of BDA Process, Benefits and Challenges of BDA", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 4, pp. 189–196, 2017. doi: 10.25046/aj020425
- Michael Fries, Markus Lienkamp, "Predictive Technology Management for the Identification of Future Development Trends and the Maximum Achievable Potential Based on a Quantitative Analysis", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 3, pp. 1042–1049, 2017. doi: 10.25046/aj0203132
- Akram Elomari, Larbi Hassouni, Abderrahim Maizate, "The main characteristics of five distributed file systems required for big data: A comparative study", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 4, pp. 78–91, 2017. doi: 10.25046/aj020411
- Martín, María de los Ángeles, Diván, Mario José, "Applications of Case Based Organizational Memory Supported by the PAbMM Architecture", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 3, pp. 12–23, 2017. doi: 10.25046/aj020303
- Jesús Morán, Bibiano Rivas, Claudio de la Riva, Javier Tuya, Ismael Caballero, Manuel Serrano, "Configuration/Infrastructure-aware testing of MapReduce programs", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 1, pp. 90–96, 2017. doi: 10.25046/aj020111
- Dillon Chrimes, Belaid Moa, Mu-Hsing (Alex) Kuo, Andre Kushniruk, "Operational Efficiencies and Simulated Performance of Big Data Analytics Platform over Billions of Patient Records of a Hospital System", Advances in Science, Technology and Engineering Systems Journal, vol. 2, no. 1, pp. 23–41, 2017. doi: 10.25046/aj020104
