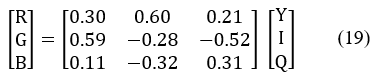A Comparative Study For Color Systems Used In The DCT-DWT Watermarking Algorithm
Volume 1, Issue 5, Page No 42-49, 2016
Author’s Name: Khalid A. Al-Afandya),1, El-Sayed M. EL-Rabaie1, Fathi E. Abd El-Samie1, Osama S. Faragallah2, Ahmed ELmhalaway2, A. M. Shehata2
View Affiliations
1Faculty of Electronic Engineering, Electronic and Communication Department, Menoufia University, Egypt
2 Faculty of Electronic Engineering, Computer Engineering and Science Department, Menoufia University, Egypt
a)Author to whom correspondence should be addressed. E-mail: Khalid_yuosif@yahoo.com
Adv. Sci. Technol. Eng. Syst. J. 1(5), 42-49 (2016); ![]() DOI: 10.25046/aj010508
DOI: 10.25046/aj010508
Keywords: Watermarking, Discrete Cosine Transform, Discrete Wavelet Transform, HSV, YIQ
Export Citations
This paper presents a comparative study of using different color systems on watermarking algorithms. This comparison aim is to determining the robustness and the stability of the color systems used in the watermarking scheme. The watermarking algorithm that is used in this paper is a hybrid scheme using the Discrete Wavelet Transform (DWT) in the Discrete Cosine Transform (DCT) domain. The DCT-DWT watermarking algorithm is applied using three color systems, the RGB (Red, Green and Blue) color system, the HSV (Hue, Saturation and Value) color system and the YIQ color system. The comparison is based on visualization to detect any degradation in the watermarked image, the Peak Signal-to-Noise Ratio (PSNR) of the watermarked image, the Normalized Correlation (NC) of the extracted watermark after extraction, the embedding algorithm CPU time, and applying different types of attacks and then calculating the PSNR and the NC.
Received: 17 September 2016, Accepted: 12 October 2016, Published Online: 27 October 2016
1. Introduction
Information technology such as digital data and multimedia can be easily duplicated, manipulated, and distributed in this time, so it’s very important to have a copyright protection to save owners copyrights. There are many protection techniques, one of them is watermarking. Watermarking technology is the process of hiding an image called watermark or label into original digital data (image, video or audio) [1,2]. Watermarking schemes can be classified into two categories; spatial domain and transform domain [3]. There are several schemes of transform domain watermarking technology. One of these schemes is the Discrete Wavelet Transform (DWT) [1,3]. It is based on dividing an image into four non-overlapping bands. These bands are calculated in different frequencies; approximation sub-band (low frequency LL), horizontal sub-band (high frequency LH), vertical sub-band (high frequency HL), and diagonal sub-band (high frequency HH) [1,3]. Other used scheme of transform domain is the Discrete Cosine Transform (DCT) [5]. This transform is used to convert spatial domain image into discrete transform domain [6]. The watermarking scheme based on transform the color image to 2D DCT for each color channel, embedding watermark into the DCT frequency, then the inverse DCT given watermarked image [5,6]. Hybrid schemes are used in watermarking schemes. One of them is DCT-DWT [7]. It is based on dividing the color image into 2D matrices. The DCT domain is extracted by applying the DCT for each 2-D matrix. Embedding watermark is done on the sub-band LL by utilize the DWT to divide the DCT domain into four sub-bands for each 2-D matrix [7-9].
Colors are an important communication tool for human; it is used for communication with outside environments [10]. Using colors in image processing improve the image data for better human understanding [10]. So it’s important to represent colors as mathematical formulas. There are different color formats that can represent the image color information; they are called the color systems. One of these color systems is the RGB color system. It is an additive color system based on tri-chromatic theory, easy to implement and very common but non-linear with visual perception [11]. Other color system is the HSV (Hue, Saturation and Value) color system. It is a linear transform from the RGB color system. It is very easy to select a desire hue and modifying it by adjusting its saturation and value [11]. Another color system is the YIQ color system. It is an analogue space of NTSC (National Television Standard Committee) system and used for color TV [10]. It is separate the RGB color system into a Luminance Y, and two chrominance information I,Q, it is useful in compression application [11].
The main aim of this paper is to apply the DCT-DWT watermarking algorithm using the RGB, the HSV and the YIQ color systems. A comparative study is done to determine the stability and the robustness of these three color systems after applying the watermarking algorithm.
The rest of this paper is organized as follows. Section 2 gives a description of the watermarking schemes. The color systems are shown in section 3. Section 4 shows the comparative topics. The simulation results are illustrated in section 5. Section 6 presents the conclusion followed by the most relevant references.
2. Watermarking Schemes
2.1. Discrete Wavelet Transform (DWT)
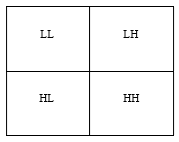
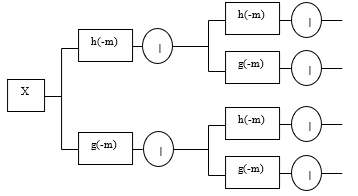
Wavelet transform is an information processing method; it has been widely used in many fields including image processing. The DWT divide an image into four non-overlapping bands. These bands are calculated in different frequencies [1]. Figure 1 shows the four sub-bands; approximation sub-band ci (low frequency LL), horizontal sub-band (high frequency LH) chi, vertical sub-band (high frequency HL) cvi, and diagonal sub-band (high frequency HH) cdi. Figure 2 show the low pass and high pass analysis filter h[-m], g[-m] while the corresponding low pass and high pass synthesis filter are h[m] and g[m]; ci and di are the low and high band output coefficient at level i [1,3].
The DWT analysis is given by:
| ci+1[m,n] = (ci(m,n)*h[-m])↓2 | (1) |
| di+1[m,n] = (ci(m,n)*g[-m])↓2 | (2) |
So the DWT synthesis is given by
| Ci+1[m,n] = [(ci(m,n)↑2)*h[m]) + [(di(m,n)↑2)*g[m])] | (3) |
Where * denotes convolution and ↑↓ denotes down sampling and up sampling by factor of 2.
2.2. Discrete Cosine Transform (DCT)
Discrete Cosine Transform (DCT) is a standout amongst the most well-known orthogonal change strategies utilized as a part of picture preparing. High vitality compaction property of the DCT is the reason. In watermarking, this property helps in choosing the area in image to insert the watermark with the most robustness [4]. The DCT divides aircraft carrier signal into three frequencies bands namely low, middle, and heights frequency bands. It is a frequency orbit watermarking scheme as the watermark is embedded into one of these three bands, carrier signal pixel are not modified directly [5].
Two dimension discrete cosine transform 2D-DCT is defined as [6]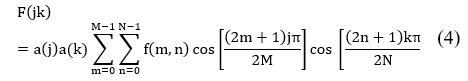
Inverse transform 2D-IDCT is defined as [6]
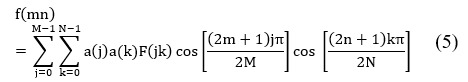 Where M,N are image dimension,
Where M,N are image dimension,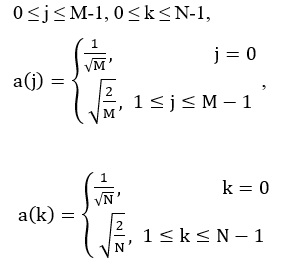
2.3. The Hybrid Scheme DCT-DWT
The hybrid scheme DCT-DWT is based on utilized the DWT to divide the DCT domain into four sub-bands [7]. The color image is divided into three 2D matrices (depending on used color system). The DCT domain is extracted by applying the DCT for each 2D matrix. Embedding watermark is done on the sub-band LL by utilize the DWT to divide the DCT domain into four sub-bands for each 2D matrix [7-9].
3. Color System
3.1. The RGB (Red, Green and Blue) Color System
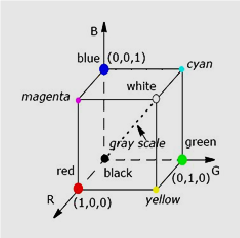
The RGB color system is an additive color system based on tri-chromatic theory, easy to implement, and very common, but non-linear with visual perception. It may be visualized as a cube with the three axis’s corresponding to red, green and blue, this cube bottom corner when Red=Green=Blue=0 and opposite top corner when Red=Green=Blue=255. The RGB color system is frequently used in most computer applications [11]. In computer applications the RGB color image represented as a three dimensional array with dimension M´N´3, where M´N is image axis X,Y and 3 is the three color channel Red, Green and Blue respectively [10]. Figure 3 show the RGB color model [10].
|
|
3.2. The HSV Color System
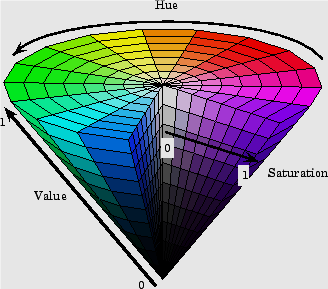
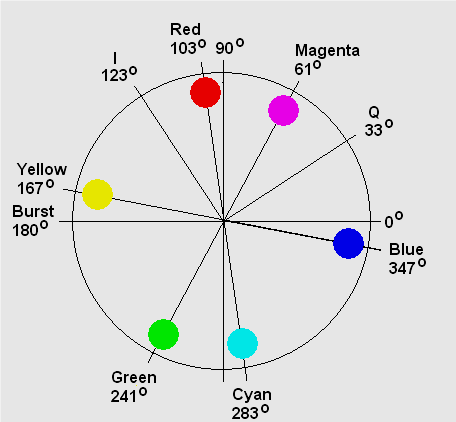
The HSV color system is a linear transform from the RGB color system. It is very easy to select a desire hue and modifying it by adjusting its saturation and value. It is defined as a position on a circular plane around the value axis. Hue is the angle from a nominal point around the circle to the color. Saturation is the radius from the central value axis to the color. Figure 4 show the HSV color model [10]. Conversion from the RGB color system to HSV color system as [11]:
Find the maximum and minimum values from the RGB triplet
 If max=min then the image is monochrome (not color) because it is no Hue
If max=min then the image is monochrome (not color) because it is no Hue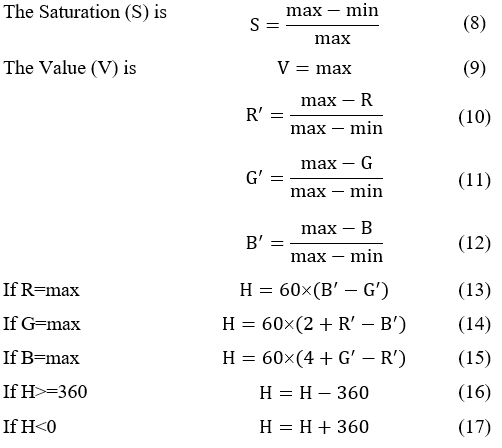
3.3. The YIQ Color System
The YIQ color system is an analogue space of the NTSC system that used for the American color TV. It separates the RGB color system into a Luminance Y, and two chrominance information I, Q. It is useful in compression application [11]. The YIQ system was designed to utilize sensitivity in luminance changes than hue or saturation changes. Figure 5 show the YIQ color system model [10]. The relation between the YIQ color system and the RGB color system as [11]:
|
|
4. The Comparative Topics
The aim of this paper is to present a comparative study of three different color systems used in watermarking scheme algorithms. The comparison is based on applying the DWT-DCT watermarking scheme algorithm for color images (host and watermark) using the RGB color system, the HSV color system and the YIQ color system. The DCT-DWT watermarking scheme is based on separation for each of the host and watermark color image into three 2-D matrices according to the used color system. The DCT domain is extracted by applying the DCT on each 2-D matrix extracted from color image. The DWT is utilized to divide the DCT domain for each 2-D matrix into four non-overlapping bands. The watermark is embedded into the LL sub-band [7-9]. A comparison is done between the three color systems RGB, HSV and YIQ. The comparison is based on visual detection, the PSNR, the NC, the embedding algorithm CPU time, and applying attacks to determine the robustness of color systems.
5. Simulation Results
All tests were performed using an Intel® core™i5 CPU M450 @2.4GHz with 6GB Memory and running Windows 7 64-bit operating system and using MATLAB 8. The images used are RGB colored JPEG images with size 512´512, and bit depth 24 host image Rokayya with resolution 72´72 dpi and watermark cats with resolution 180´180 dpi as shown in Figure 6. There are five main tests to determine the performance of a color system used in watermarking scheme algorithm. Visually test to determine the invisibility of watermark in the watermarked image and any degradation in colors compared to original image, the embedding algorithm CPU time, the Peak Signal-to-Noise Ratio (PSNR) of the watermarked image, the Normalized Correlation (NC) for the extracted watermark are calculated, and applying attacks on the watermarked image then extracting the watermark and calculating the PSNR and the NC again after attacks. PSNR can be calculated by [5]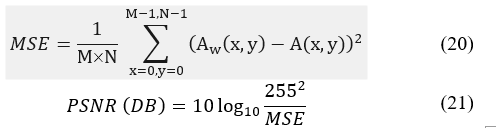
where A is original image, Aw is watermarked image and M, N size of original and watermarked image. NC calculate given by [5]
![]() Where W is original watermark and W* is extract watermark
Where W is original watermark and W* is extract watermark
|
|
|
|
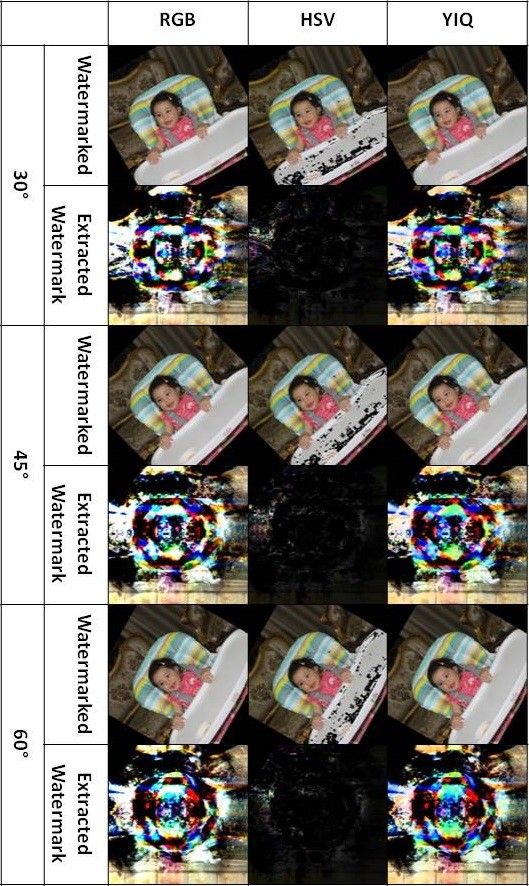
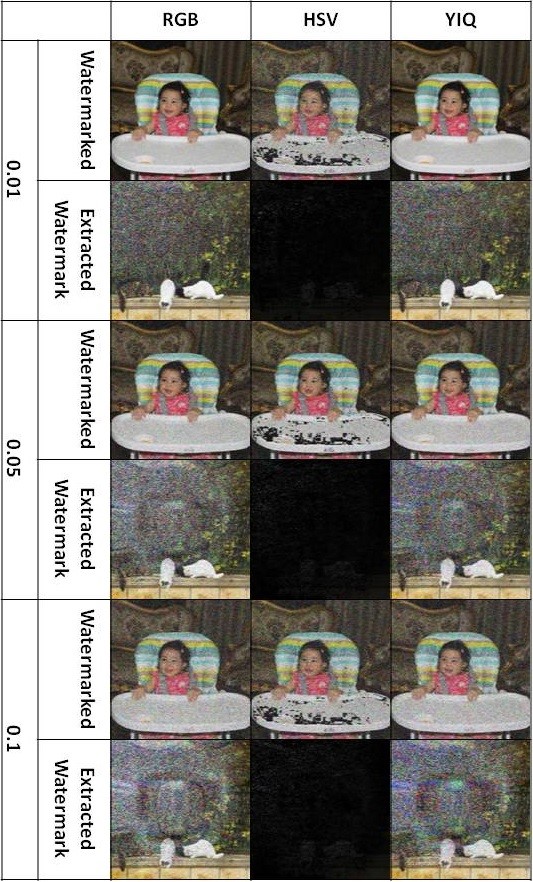
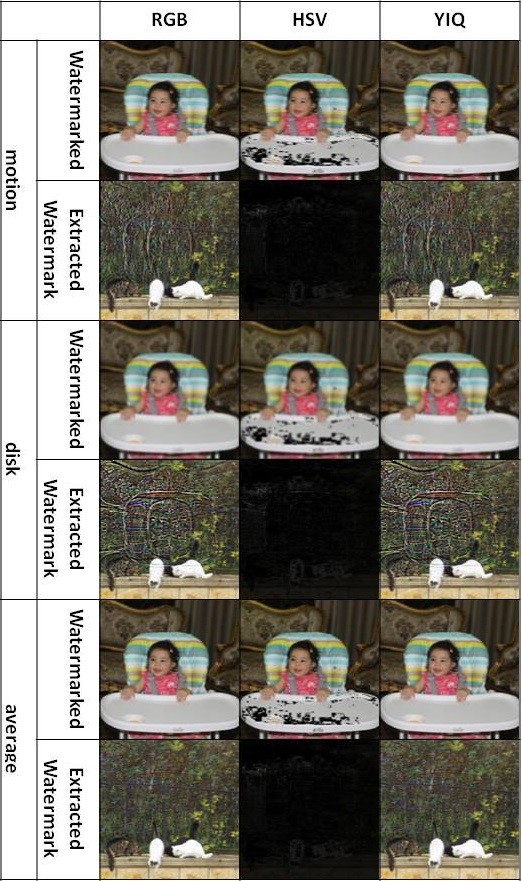
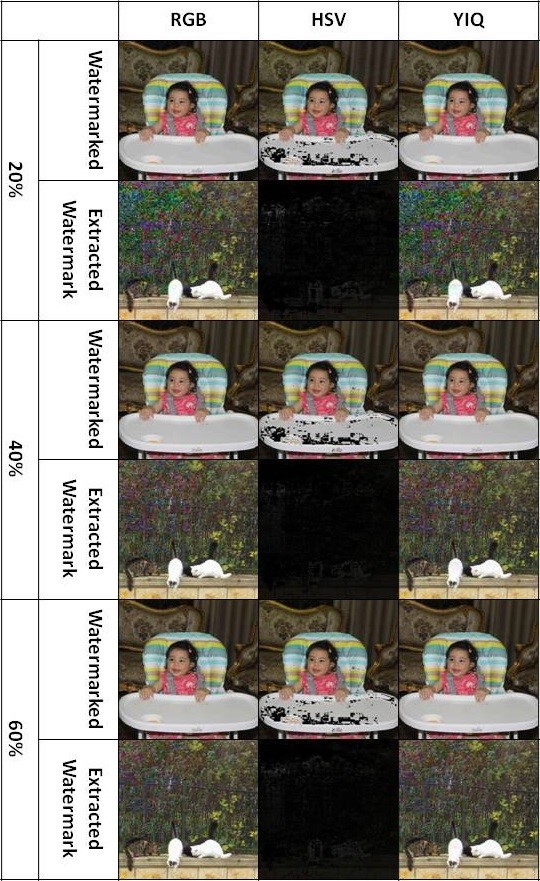
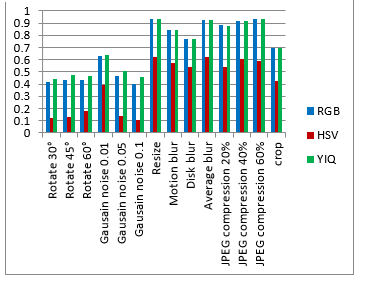
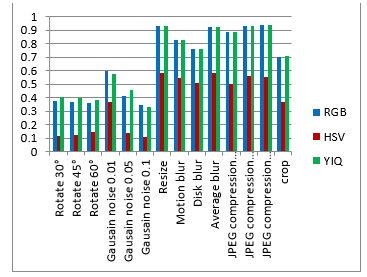
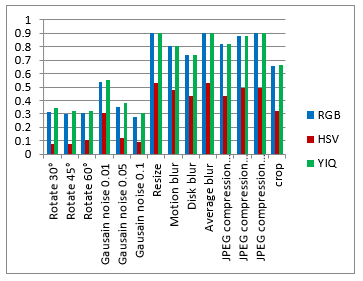
Visualization comparison results without attacks are shown in figure 7. Figure 8 shows the rotate attacks (30°, 45° and 60°). Gaussian noise attacks are shown in figure 9 with variance parameters (0.01, 0.05 and 0.1). Figure 10 shows the blur attacks (motion, disk and average). The JPEG compression attacks are shown in figure 11 (20%, 40% and 60%). Figure 12 shows the resize to 256´256 attacks then resize to 512´512. The crop attacks are shown in figure 13. The evaluation matrices results (PSNR and NC) without attacks and embedding algorithm CPU time for the comparison are shown in table1 and figure 14. Table 2 and figure 15 show the evaluation matrices results (PSNR and NC) after attacks.
|
|
|
|
|
|
|
|
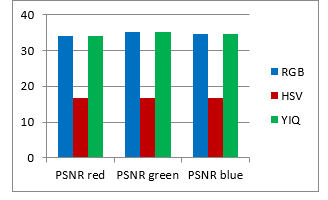
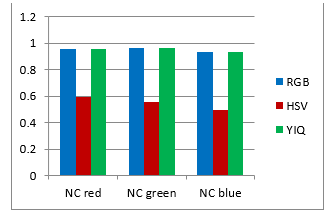
| Without attack | RGB | HSV | YIQ |
| PSNR red | 33.9764 | 16.6698 | 33.9764 |
| PSNR green | 35.2180 | 16.6828 | 35.2180 |
| PSNR blue | 34.6320 | 16.6906 | 34.6320 |
| NC red | 0.9587 | 0.5927 | 0.9585 |
| NC green | 0.9646 | 0.5554 | 0.9644 |
| NC blue | 0.9377 | 0.4997 | 0.9373 |
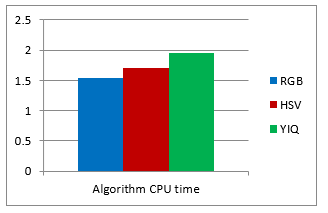
| CPU time (Sec) | 1.5444 | 1.7004 | 1.95 |
| Table 1. The PSNR for watermarked image, the NC for extracted watermark without attacks and the CPU time for embedding algorithm. |
|
Figure 14. The evaluation matrices comparison based on the PSNR for watermarked image, the NC for extracted watermark without attacks and the CPU time for embedding algorithm.
|
|
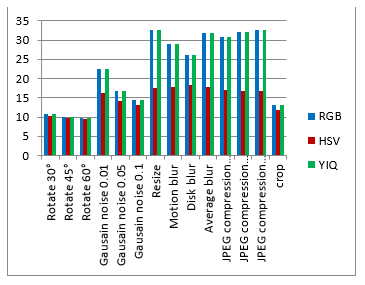
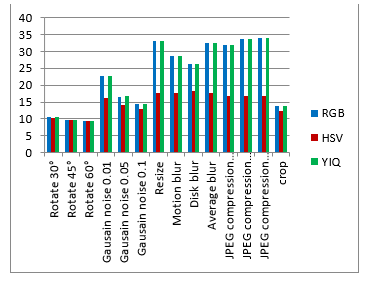
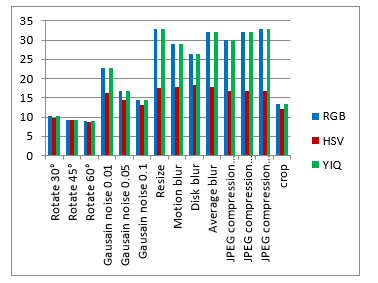
Table 2. The PSNR for watermarked image, and the NC for extracted watermark after attacks.
|
| After attack | RGB | HSV | YIQ | |
| Rotate 30° | PSNR red | 10.8712 | 10.2095 | 10.8712 |
| PSNR green | 10.7056 | 10.1637 | 10.7056 | |
| PSNR blue | 10.2787 | 9.7696 | 10.2787 | |
| NC red | 0.4134 | 0.1261 | 0.4385 | |
| NC green | 0.3737 | 0.1128 | 0.4029 | |
| NC blue | 0.3110 | 0.0758 | 0.3429 | |
| Rotate 45° | PSNR red | 10.0475 | 9.7151 | 10.0475 |
| PSNR green | 9.7717 | 9.5316 | 9.7717 | |
| PSNR blue | 9.3565 | 9.1425 | 9.3565 | |
| NC red | 0.4349 | 0.1309 | 0.4709 | |
| NC green | 0.3691 | 0.1242 | 0.4000 | |
| NC blue | 0.2992 | 0.0773 | 0.3192 | |
| Rotate 60° | PSNR red | 9.6386 | 9.4558 | 9.6386 |
| PSNR green | 9.4120 | 9.3174 | 9.4120 | |
| PSNR blue | 8.9305 | 8.8420 | 8.9305 | |
| NC red | 0.4347 | 0.1782 | 0.4660 | |
| NC green | 0.3594 | 0.1484 | 0.3848 | |
| NC blue | 0.3049 | 0.1052 | 0.3219 | |
| Gaussian noise 0.01 | PSNR red | 22.5692 | 16.1464 | 22.5873 |
| PSNR green | 22.6814 | 16.1505 | 22.6942 | |
| PSNR blue | 22.6411 | 16.1870 | 22.6542 | |
| NC red | 0.6281 | 0.3893 | 0.6381 | |
| NC green | 0.5946 | 0.3712 | 0.6014 | |
| NC blue | 0.5402 | 0.3044 | 0.5505 | |
| Gaussian noise 0.05 | PSNR red | 16.6907 | 15.2738 | 16.6774 |
| PSNR green | 16.6384 | 14.2272 | 16.6643 | |
| PSNR blue | 16.7434 | 14.3356 | 16.7488 | |
| NC red | 0.4637 | 0.1376 | 0.5034 | |
| NC green | 0.4144 | 0.1350 | 0.4472 | |
| NC blue | 0.3507 | 0.1189 | 0.3807 | |
| Gaussian noise 0.1 | PSNR red | 14.4521 | 13.0484 | 16.4830 |
| PSNR green | 14.3016 | 12.9226 | 14.3182 | |
| PSNR blue | 14.4515 | 13.0859 | 14.4692 | |
| NC red | 0.4015 | 0.1027 | 0.4555 | |
| NC green | 0.3481 | 0.1054 | 0.3887 | |
| NC blue | 0.2765 | 0.0936 | 0.3104 | |
| Resize | PSNR red | 32.6509 | 17.5709 | 32.6509 |
| PSNR green | 33.2573 | 17.5776 | 33.2573 | |
| PSNR blue | 32.9487 | 17.5823 | 32.9487 | |
| NC red | 0.9318 | 0.6209 | 0.9316 | |
| NC green | 0.9333 | 0.584 | 0.9329 | |
| NC blue | 0.9050 | 0.5326 | 0.9045 | |
| Motion blur | PSNR red | 28.9065 | 17.6938 | 28.9065 |
| PSNR green | 28.7466 | 17.6686 | 28.7466 | |
| PSNR blue | 28.8790 | 17.6937 | 28.879 | |
| NC red | 0.8434 | 0.5767 | 0.8438 | |
| NC green | 0.8284 | 0.5423 | 0.8291 | |
| NC blue | 0.8024 | 0.4743 | 0.8038 | |
| Disk blur | PSNR red | 26.1620 | 18.2997 | 26.1620 |
| PSNR green | 26.3194 | 18.3153 | 26.3194 | |
| PSNR blue | 26.3862 | 18.3299 | 26.3862 | |
| NC red | 0.7696 | 0.5386 | 0.7702 | |
| NC green | 0.7600 | 0.5101 | 0.7620 | |
| NC blue | 0.7346 | 0.4336 | 0.7374 | |
| Average blur | PSNR red | 31.9021 | 17.6811 | 31.9021 |
| PSNR green | 32.4367 | 17.6901 | 32.4367 | |
| PSNR blue | 32.1206 | 17.6905 | 32.1206 | |
| NC red | 0.9250 | 0.6214 | 0.9247 | |
| NC green | 0.9269 | 0.5835 | 0.9265 | |
| NC blue | 0.8990 | 0.5307 | 0.8984 | |
| JPEG compression 20% | PSNR red | 30.8030 | 16.9024 | 30.8030 |
| PSNR green | 31.8857 | 16.9348 | 31.8857 | |
| PSNR blue | 30.1031 | 16.8905 | 30.1031 | |
| NC red | 0.8804 | 0.5430 | 0.8792 | |
| NC green | 0.8892 | 0.5023 | 0.8883 | |
| NC blue | 0.8225 | 0.4338 | 0.8209 | |
| JPEG compression 40% | PSNR red | 32.0421 | 16.8709 | 32.0421 |
| PSNR green | 33.8185 | 16.9056 | 33.8185 | |
| PSNR blue | 32.1418 | 16.8881 | 32.1418 | |
| NC red | 0.9186 | 0.6038 | 0.9181 | |
| NC green | 0.9319 | 0.5630 | 0.9311 | |
| NC blue | 0.8809 | 0.4939 | 0.8797 | |
| JPEG compression 60% | PSNR red | 32.5064 | 16.6962 | 32.5064 |
| PSNR green | 33.9616 | 16.7221 | 33.9616 | |
| PSNR blue | 32.8417 | 16.7128 | 32.8417 | |
| NC red | 0.9345 | 0.5899 | 0.9341 | |
| NC green | 0.9423 | 0.5560 | 0.9417 | |
| NC blue | 0.9036 | 0.4939 | 0.9025 | |
| Crop | PSNR red | 13.2283 | 11.8709 | 13.2283 |
| PSNR green | 13.6797 | 12.1924 | 13.6797 | |
| PSNR blue | 13.5194 | 12.0834 | 13.5194 | |
| NC red | 0.6993 | 0.4286 | 0.6991 | |
| NC green | 0.7009 | 0.3664 | 0.7056 | |
| NC blue | 0.6567 | 0.3253 | 0.6645 | |
|
|
|
|
|
|
|
|
|
|
|
|
|
Figure 15. The evaluation matrices comparison based on the PSNR for watermarked image, and the NC for extracted watermark after attacks.
|
As shown from visualization test, experimental results and evaluation figures with and without attacks, results illustrate that; there is a degradation in colors for the watermarked images and the extracted watermark is not good for using the HSV color system, where there are no degradation in colors for the watermarked images and the extracted watermarks are good for using the RGB and the YIQ color systems. The PSNR and the NC values without and after attacks for the HSV color system are less than the RGB and the YIQ color systems. The PSNR and the NC values without attacks for the RGB color system are little higher than the YIQ color system. The PSNR and the NC values after some attacks for the YIQ color system are little higher than the RGB color system and similar after other attacks. The Embedding algorithm CPU time show that the RGB color system is the faster and the slower is the YIQ color system but the difference is fractions of second so that the three color systems are approximately similar in embedding algorithm CPU time.
The HSV color system is worse than the RGB and the YIQ color systems and weak against attacks. The RGB color system and the YIQ color system are approximately similar and robust against attacks.
6. Conclusion
This paper presents a comparison between three different color systems; the RGB color system, the HSV color system, and the YIQ color system in watermarking algorithms. This comparison is to determine the stability and the robustness of color systems that used for applying the watermarking schemes. The watermarking algorithm that is used in this paper is the hybrid scheme DCT-DWT. This comparison illustrates that the HSV color system is the weakest when compared to the RGB and the YIQ color systems and is not robust against attacks. The RGB color system and YIQ color system are approximately similar and robust against attacks. The YIQ color system is a little robust against attacks when compared to the RGB color system. The embedding algorithm CPU time using the RGB color system is a little faster than the HSV and the YIQ color systems; the difference is a fraction of second. The results reveal the superiority of using the RGB and the YIQ color systems over the HSV color system.
- Giri, Kaiser J., Mushtaq Ahmad Peer, and P. Nagabhushan, “A robust color image watermarking scheme using discrete wavelet transformation”, International Journal of Image, Graphics and Signal Processing (IJIGSP), 7(1): 47-52 (2014).
- Saini, Mandeep Singh, B. Venkata Kranthi, and Gursharanjeet Singh Kalra, “Comparative analysis of digital image watermarking techniques in frequency domain using MATLAB SIMULINK”, International Journal of Engineering Research and Applications (IJERA), 2(4): 2248-9622 (2012).
- Ganjir, Neha, and Nivedita Singh, “Bi-orthogonal wavelet transform based 3-D image watermarking on colour image”, International Journal of Computer Science and Mobile Computing, 3(8): 451-456 (2014).
- Kekre, Dr HB, Dr Tanuja Sarode, and Shachi Natu, “Hybrid watermarking of colour images using DCT-Wavelet, DCT and SVD”, International Journal of Advances in Engineering and Technology, 6(2): 769-779 (2013).
- Jiansheng, Mei, Li Sukang, and Tan Xiaomei, “A digital watermarking algorithm based on DCT and DWT”, International Symposium on Web Information Systems and Applications (WISA’09), 9(1): 104-107 (2009).
- Saini, Lalit Kumar, and Vishal Shrivastava., “Analysis of attacks on hybrid DWT-DCT algorithm for digital image watermarking with MATLAB”, International Journal of Computer Science Trends and Technology (IJCST), 2(3): 123-126 (2014).
- Mukherjee, Pameli, and Saurabh Mitra., “A review on copy-move forgery detection techniques based on DCT and DWT”, International Journal of Computer Science and Mobile Computing, 4(3): 702-708 (2015).
- Benoraira, Ali, Khier Benmahammed, and Noureddine Boucenna., “Blind image watermarking technique based on differential embedding in DWT and DCT domains”, EURASIP Journal on Advances in Signal Processing, 2015(1): 1-11 (2015).
- Kaur, Ramandeep, and Jatinder Kumar., “Integrated DCT, DWT and modified SVD based digital image watermarking”, International Journal of Computer Science and Mobile Computing, 4(5): 1002-1011 (2015).
- Noor A. Ibraheem, Mokhtar M. Hasan, Rafiqul Z. Khan and Pramod K. Mishra, “Understanding color models: a review”, ARPN Journal of Science and Technology, 2(3): 265-275 (2012).
- Adrian Ford, and Alan Roberts, Colour Space Conversions, Westminster University, London, 1-31 (1998).