A Systematic Mapping Study of Cloud, Fog, and Edge/Mobile Devices Management, Hierarchy Models and Business Models
Volume 4, Issue 2, Page No 91-101, 2019
Author’s Name: Isaac Odun-Ayo1,a), Rowland Goddy-Worlu1, Victor Geteloma1, Emanuel Grant2
View Affiliations
1Department of Computer and Information Sciences, Covenant University, 112233, Nigeria
2School of Electrical Engineering & Computer Science, University of North Dakota, 58202, USA
a)Author to whom correspondence should be addressed. E-mail: isaac.odun-ayo@covenantuniversity.edu.ng
Adv. Sci. Technol. Eng. Syst. J. 4(2), 91-101 (2019); ![]() DOI: 10.25046/aj040212
DOI: 10.25046/aj040212
Keywords: Cloud computing, Fog computing, Edge computing
Export Citations
Cloud computing is an exceptional paradigm, which is facilitating the developments and utilization of resources over the internet. Fog computing operates at the edge of the network saving bandwidth, by not sending all information to the cloud, while edge computing does processing of data at the edge of the cloud. Edge computing reduces the distance data must travel on the network. The unique relationship between cloud, fog and edge computing makes research in these areas mandatory. Deciding on a specific area of research as regards these subjects could be a bulky procedure for a scientist. Therefore, reviews and paper studies for recognizing potential research gaps are required. A systematic mapping study is utilized in giving a summary of the conducted research in a particular study area. The objective of this paper is to conduct systematic mapping studies on cloud, fog, edge/mobile devices management, hierarchy models and business models. The results showed that publications that discussed process in relations to the field of study is 14.04% out of the 114 papers included. Also method contributed 24.56%, model had 42.98% and tool contributed 18.42%. Furthermore, evaluation research in terms of the field of study was 27.5% out of 120 papers included. Also, validation was discussed in 17.5% of the papers, solution was 32.5%, philosophical was 5.83%, experience was 15.83% and opinion was 0.83%. The clearly highlighted gaps ought to inspire more enthusiasm for additional research by both researchers and industry practitioners.
Received: 10 January 2019, Accepted: 22 February 2019, Published Online: 15 March 2019
1. Introduction
The Cloud is a parallel and appropriated computing system comprising of interconnected and virtualized computers that are powerfully displayed as a unified computing resource, which is dependent on service level approvals set up through dealings between service providers and users [1]. Cloud computing is basically interconnected computers and applications used to deliver services over the Internet. When systems are connected in this manner, device management also becomes paramount. Cloud computing is presently delivering services at all layers hence, there is everything as a service, but there are three primary services in the cloud which are Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS) and Infrastructure-as-a-Service (IaaS). In SaaS, major cloud service provider (CSP) like Salesforce.com offer custom-built applications for users on the internet, hence the user do not need to bother about installation and license. In PaaS, the user develops and deploys his application through the infrastructure made available by the CSP. In IaaS, the user utilized resources on the CSP infrastructure on a pay as you go basis. The CSPs have massive data centers with state of the art system; hence, the user can start up without the cost of infrastructure. Although the CSPs strive in providing effective and trustworthy services on the cloud, there are also issues of trust [2]. The effectiveness of cloud computing becomes very evident as services improve and expand regularly, due to the fundamental applications running on the cloud [3,4]. In addition, there are four cloud computing models namely the private, public, community and hybrid models. Private clouds provide organizations infrastructures that are hosted on premises or off premises making use of in house staff. Private clouds are considered more secure. Public clouds provide massive elastic, on-demand pool of resources to the users through the CSP infrastructure. Community cloud make services available to institutions that share infrastructure but operate independently. Hybrid clouds provide the potential to host core applications on private cloud and auxiliary applications on public clouds. However, due to the process of virtualization and multitenancy on the cloud, there are concerns about security [5,6].
Fog and edge computers carry out storage and processing at the edge of the cloud. This saves bandwidth and makes usage simple. However, there are technologies that must be used to monitor these applications data and services operating within and at the edge of cloud computing. Edge computing is characterized by proximity to end users, zone geographical distribution, and support for high mobility and value addition for customer IoT services [7]. Mobile edge computing aims at reducing both network latency and resource demand by shifting computing and storage capacities from the Internet cloud to the mobile edge [8]. In [9], the cloud system is described with a 3-layer hierarchy, the cloud computing infrastructure layer, the edge computing or mobile clouds, which are utilized in vertically integrated applications where a part of the processing and analytics happens on the edge device while the cloud is used for coordination and data retrieval [10]. The service measurement index framework discussed in [11] is a business model that provides an understanding of CSP rankings, and has 7 major characteristics namely: accountability, agility, assurance, financial, performance, security and privacy and usability [11].
Systematic mapping studies provides a platform for categorizing research using a scheme and structure indicating the frequency of research in such an area and the results are presented visually on a map. Systematic mapping requires less effort: yet provides a more coarse-grained overview in the area of study [12]. This enables the coverage of the research field to be determined. The systematic process in this work was accomplished using three facets: the topic, contribution and research facets. The topic facet extracts key consideration from the scope of study. The contribution facet deals with method or mode of the work, while the research facet considers the nature of research such as evaluation or opinion. While the goal of this study is to conduct a systematic mapping study, the rest of the paper is organized as follows: Section II examines the related work. Section III examines the materials and methods, Section IV presents the results and discussion and Section V is the conclusion and suggestion for future work.
2. Related Work
In [13], the authors explored the developing stage of a systematic mapping study by identifying the software designs present at the requirement engineering stage of the project, and providing a comprehension of the roles played by these patterns based on basic parameters required in the development process. A protocol was developed for the study with basic steps to enable the replication of their work by the research community, which results in confirming the validation of the research. For this paper, ACM DL, IEEExplore, SCOPUS, and Web of Science digital libraries were utilized, and the guidelines laid down in [12] were adhered to.
In [14], the authors dwelled on describing the protocol for a systematic map, in relation to domain-specific languages (DSL). The authors focused on channeling their work on the advanced apprehension of the DSL domain of research, while emphasizing on trending researches and subsequent expectations, and utilizing the requirements for conducting a systematic review, all within the interval of July 2013 to October 2014.
The authors in [15] analyzed the utilization of concept maps in Computer Science, which resulted in a systematic map focused on gathering and analyzing previous articles on concept maps. This resulted in a thorough examination of concept maps, with emphasis on learning and teaching supports. Also, the searching process involved the utilization of backward snowballing and manual methods, and search strings applied on SCOPUS, ScienceDirect, Compedex, ACM DL, and IEEExplore digital libraries.
In [16], the researchers examined how games related methods are implemented in software engineering, and how these methods assist specified software engineering knowledge domains. Based on publications from 1974 to 2016, the authors utilized 156 primary studies, which were centered on using and evaluating games in software engineering education. The mapping procedure was done in line with the guidelines provided in [12].
In [17], the authors did a mapping of power system model by providing a summary of power system models and its subsequent usage by European organizations in terms of analysis of their modeling features and identification of modeling gaps. 228 surveys were sent out to power experts for data extraction, while 82 questionnaires were eventually completed and utilized for the mapping.
In [18], a mapping study of domain-specific languages was conducted with a primary interest in the type of contribution and research, and the area of focus. By exploring reputable articles from 2006 to 2012, a mapping study was conducted by defining research questions, conducting the search, and extracting the data.
In [19], the authors focused on searching studies on “legal theory” and “legal concepts”. The selected studies were grouped on contributions in terms of language, tool, method, and model. The other steps include identification of the used legal theories in legal core ontologies building process, identification of focus with a clear recommendation on the use of two ontologies, and analyzing each highlighted research for conclusive findings about legal and ontological research.
In [20], the researchers gave a summary of an empirical research in software cloud-based testing in the process of building a classification scheme. The authors examined functional and non-functional testing techniques, their applications, and their peculiarities. Sixty-nine (69) primary studies out of seventy-five (75) research articles were utilized for a rigorous statistical analysis, and an eventual quantitative result. Most articles utilized a singular experiment approach for evaluating their expected result.
In [21], the authors presented a comprehensive review of knowledge management in organization with a focus on the potential role of Information Technology (IT) in the process. They further discussed several important issues bordering on the process of managing knowledge and the role of IT in propelling and assisting these processes. Also, emphasis was made on the need to support in creating, storing, transferring and applying knowledge in organizations.
In [22], the authors discussed the usefulness and limitations of systematic literature review in information system and social sciences. They are of the opinion that the general stand that systematic literature review provide a holistic and superior approach to literature review is not only questionable but also unacceptable. In their argument and justification of this, they concluded that caution and restrains should be exercised when choosing systematic literature review as it could undermine critical engagement with literature and the scholarly nature of academic work.
In [23], the authors discussed the lessons learned from utilizing a systematic literature review process on software engineering domain. The authors summarized the review process, highlighted the reviews of other authors and finally extracted and discussed findings as regards applying this practice to software engineering domain.
In [24], the researchers opined that research reviews must pay close attention to rigorous methodology that is required of primary researcher. The author further conceptualized the research review as a scientific enquiry involving five stages that parallel those primary research, which includes: formulating the problem, collecting data, evaluating the data points, analyzing and interpreting the data, and lastly, presenting the results. All the functions; sources of variance and the other potential treats to validity with each stage are discussed.
In [25], the authors provided useful insights to researchers for carrying out literature review. They suggested synthesizing trends and patterns while preparing to write literature review, among which includes: the purpose and voice before beginning to write must be considered, then consider how to reassemble the notes as well as create a topical outline that traces the argument in the literature review. All of these provides the guidelines for developing a thorough and coherent literature review.
In [26], the researchers assessed the effectiveness of a systematic literature review, which recommends evidence-based software engineering methods for aggregating evidence. The authors utilized manually searched Journals (10) and conference proceedings (4). Of the twenty (20) significant articles considered, eight (8) articles focused on research trends rather than evaluating the technique utilized, and seven (7) systematic literature reviews focused on estimating the cost. The quality of systematic literature reviews was fair with only three scoring less than 2 out of 4.
In [27], the authors have an opinion that the evaluation of the approaches of systematic mapping, as carried out by researchers, is needed in identifying the improved guidelines that are centered on the experiences from existing systematic maps and literature reviews. In the affirmative, the authors carried out a systematic mapping study and considered a few practices of the systematic review guidelines. They discovered that amongst the extensive number of studies carried out, various guidelines were utilized and integrated, leading to multiple methods of conducting systematic mapping studies.
In [28], the authors stressed the importance of literature review in scientific enquiry and the need to avoid standing on the shoulders of dwarf literature search, which remains a point of concern for enhancing a productive literature review. The authors further discussed the difficulties of literature search in the ever-increasing dynamic setting of data frameworks, and proffer solutions on how these difficulties can be dealt with.
In [29], the authors presented the systematic mapping study of high-performance computing and the cloud which based their work on the concepts of [27]. This study provided six classes of studies in the areas of architecture, virtualization, application, optimization, design and implementation, and performances in relation to the focus of study. The selected studies were applied on the contribution facet such tool, method, and model. In addition, the selected studies were used on the research facet which dealt with evaluation, validation and solution research.
In [30], the researchers examined the systematic mapping study of cloud resources management and scalability in brokering, scheduling, capacity planning and elasticity. The classification scheme in relation to resource management, discussed scalability, brokering, scheduling, capacity planning, elasticity, and resource sharing. The selected studies were applied on the contribution facet such metric, tool, method, and model. In addition, the selected studies were applied to the types of research.
3. Materials and Methods
The systematic mapping study is a useful tool for both researchers and practitioners alike. A mapping study provides a visual representation of scope of work in a particular discipline. This study was carried out utilizing the guidelines on systematic mapping studies, as seen in [12]. Systematic mapping study involves replicating a process for deducing and interpreting accessible materials, in line with a research objective [31]. This important process (Figure 1) involves defining the research question and outlining the scope of the review. Next is screening the articles to select the important ones and key wording the abstract of the articles, with the goal of creating a classification scheme. Finally, the last step involves extracting the data, which ultimately leads to creating the systematic map. At every stage of the process there was an outcome which was refined for better overall output of the systematic map.
3.1. Definition of Research Questions
The goal of a systematic map is to provide more insight into the quantity and type of work being conducted in a particular discipline. It may also be necessary to know the places where such work were published. These issues help in determining the appropriate research questions to apply to the study in this paper.
The research questions are:
RQ 1: What areas are addressed and what number of articles are covered in the highlighted areas of the research topic?
RQ 2: What sets of articles are published in the highlighted areas and what are their evaluations and originality?
3.2. Conduct of Research for Primary Studies
For the purpose of getting papers for this study, four (4) major digital libraries based on their impact factor of conferences and journal publication were utilized. Table 1 contains the digital libraries and their corresponding uniform resource locator (URL).
Table 1: Electronic databases used for the systematic mapping study
| Electronic Databases | URL |
| ACM | http://dl.acm.org/ |
| IEEE | http://ieeexplore.ieee.org/xplore |
| SCIENCE DIRECT | http://www.sciencedirect.com/ |
| SPRINGER | http;//www.springerlink.com/ |
The search string was designed based on population, outcome and intervention of the papers. The keywords used in the research was gotten from all parts of the structure of this study’s title; the search string is as follows:
(TITLE (cloud) AND KEY (cloud) AND (TITLE-ABS-KEY) (fog) OR TITLE-ABS-KEY (edge and mobile) OR TITLE-ABS-KEY (“devices management”) AND (KEY (Models) OR TITLE (models)
The searches were performed on the electronic database, which involves utilizing the designed search string above on document metadata to guarantee the inclusion of significant articles. For this study, findings from relevant databases relating to cloud computing and computer science were utilized, and a total of 120 papers were relevant to be included out of an underlying pursuit comprising of 1339 papers. This study covered the period 2001 – 2018. The list of primary studies utilized for this work is at the Appendix.
3.3. Screening of Papers for Inclusion and Exclusion
The importance of selection criteria is identifying and incorporating all papers relevant to the study. This was a vital aspect of the study. It was essential to use the inclusion and exclusion criteria to eliminate irrelevant articles as regards to cloud, fog, and edge/models device management. In addition, the criteria was utilized in removing all materials not providing answers to the research question. Some abstract usually mention only one aspect of the focus of study without further details and such papers are also excluded. This study also excluded panel discussions, editorials, prefaces, presentation slides, summaries and tutorials. It was pertinent to consider articles that had the main focus and able to also provide some secondary details. The main focus of this study was devices management and models as it relates to cloud, fog, and computing. Therefore, the inclusion and exclusion process was done using details depicted in Table 2.
Table 2: Inclusion and exclusion criteria
| Inclusion criteria | Exclusion criteria |
| The abstract explicitly mentions cloud, fog, edge, mobile devices management, hierarchy models and business models. Furthermore, discussions in this area are meant to achieve cloud management. | The paper lies outside the area of cloud computing as it identifies with cloud management. The paper does not contribute to issues of management in the cloud. |
3.4. Keywording of Abstracts
Keyword of abstracts is an important process in systematic mapping, used to design the classification scheme for the study and involves the following stages as shown in Figure 1.
 Figure 1: The systematic mapping process [27]
Figure 1: The systematic mapping process [27]
Key wording was useful in decreasing the required time for designing a classification scheme for cloud management and model studies. Also, key wording ensured that only the significant papers were considered in the scheme. The abstracts were studied in order to extract concepts and keywords relating to the focus of this study. Therefore, keywords from different publications were combined together to give satisfactory knowledge about the nature of the contributing research. This was eventually utilized in determining the facts or categories of the study.
A cluster of keywords were finally used in this paper to determine the categories and the eventual systematic map. In this paper, the three categories focused on topics based on all aspect of the title of the study. The second facets discussed the types of contributions in relation to metric, tool, method, process and model [12]. The third facet concentrated on research types such as evaluation and validation.
3.5. Research type Facts with Category and Description
A study of this nature will be inadequate without all the categories outlined. The following is the classification of research methods, which was utilized for the third facet, as listed in [32]:
- Validation of research: The utilized methods are unique but not yet executed, either in form of an application or experiments.
- Evaluation research: The methods have been executed and analyzed with a proof of concept. Outcomes are examined in terms of advantages and disadvantages.
- Solution proposal: The method offers an essential solution to a problem; the benefits and application of such results are also outlined.
- Philosophical papers: The papers discuss techniques that provide new methods of solving a problem in relation to concepts and framework.
- Opinion papers: The research papers do not apply any known methods, but simply expressed the opinion of individuals.
- Experience papers: This paper relates the personal experience of the researcher. It offers insight into how something was done
These categories were considered adequate and sufficient to be used in the classification scheme of this study, as to research facet. The papers included in this study were all examined based on the various research categories.
3.6. Data Extraction and Mapping Studies
Relevant articles were sorted into a classification scheme at the key wording stage. This next step allowed data extraction from the primary studies. The method of extracting data shaped the nature of the classification scheme. The procedure for extracting data was achieved on Microsoft Excel tables. The Excel tables contained the various groups of the classification scheme. The frequency of publications in each category was extracted to different tables. The frequency of publications in each category was combined into a table either contenting the topic/contribution category or the topic/research category. The analysis was focused on presenting the frequencies of articles based on the entries made into the various Excel tables. The essence was to identify which aspect of device management and models as it relates to cloud, fog and edge/mobile computing were given more emphasis in this study This enabled the determination of gaps and made it easy to identify areas for further research.
Based on the results extracted to the Excel tables, bubble plots were subsequently utilized in presenting the frequency of the articles using a map. The map included a two x-y scatter plot with bubbles at the crossing point of the classifications. The size of the bubble coordinates corresponds to the quantity of articles in such combined categories. There were two quadrants based on the three facets under consideration. Each quadrant provided different visualized maps on the basis of the intersection of the topic category with either the contribution or research category. The different facets could be considered simultaneously, providing an overview of the results of the study.
4. Results and Discussion
The analysis of the result is meant to present the frequencies of publication in each category, and to identify which category has been emphasized in past research [12]. The essence of this was the identification of gaps and the possibility of researching further. From the analysis, gaps were identified by using the systematic map, which showed topic areas where there was dearth of study, and indicated the areas that were explored as regards articles. In this systematic study, high-level categories was utilized in assessing the primary studies, which was used to create the systematic map.
4.1. Topic and Contribution Facet
The topics extracted at the classification scheme in this field of study comprise of the following:
- Architecture
- Application
- Implementation
- Networking
- Mobile computing
- Embedded systems
The list of primary studies used for checking the topics against the types of contributions is at Table 3. The systematic map is shown at Figure 2. The contribution facet shows the type of contribution to the field of study. The results showed that publications that discussed process in relations to the field of study was 14.04% out of the 114 papers included. In addition, method contributed 24.56%, model had 42.98% and tool contributed 18.42%. There were no contributions at all from metric.
Models discussion contributed 42.98% of the papers reviewed. In relation to the topics, model had 5.22% in terms of architecture, 12.28% in terms of application, and 3.51% in the area of implementation, 10.53% in the area of networking, 3.51% in the aspect of mobile computing and 7.89% on embedded system. Other aspects of topic and contribution aspect are reflected in Figure 2.
4.2. Type and Research Facet
The list of primary studies used for examining the topics against the types of research is at Table 4. On the x-axis of the right quadrant of Figure 2 are the results of the types of research conducted with respect to the field of study. The result indicated that evaluation research in terms of the field of study was 27.5% out of 120 primary studies. Also, validation was discussed in 17.5% of the papers, solution in 32.5%, philosophical in 5.83%, experience in 15.83% and opinion in 0.83%.
Solution proposal constituted 32.5% of the papers examined in this field of study in relation to the topics. Solution proposal had 1.67% in terms of architecture, 8.33% in terms of applications, 5% in relation to implementation, 11.67% with respect to networking, 3.33% in terms of mobile computing and 2.5% in terms of embedded system. Other aspects of research and topic contribution is as shown in Figure 2.
4.3. Major Findings
From Figure 2,
- It can be identified from the visual map that there were more publications on implementations and mobile networking that discussed metric with 26%, more publication on applications that examined model with 12.28%, more papers on architecture that discussed method with 6.14% and more work on embedded systems examining process at 6.14%.
- Similarly, on the left quadrant of Figure 2, there were more articles on mobile computing that discussed evaluation research with 9.17%, more publications on application that examined validation research with 5%, more work on network in terms of solution proposal at 11.67%, more publication on mobile computing in terms of philosophical paper with 3.33%, more materials on application in term of experience papers and only one opinion paper related to embedded system.
- On the other hand, this study had shown that there were no discussions at all relating to metric in this field of study. There were no papers on architecture in terms of tool. There were no articles on implementation and networking in terms of process. In addition, there was no work on architecture, application, and networking in the area of philosophical papers.
- Furthermore, publications on application topic as it related to tool, mobile networking and implementation
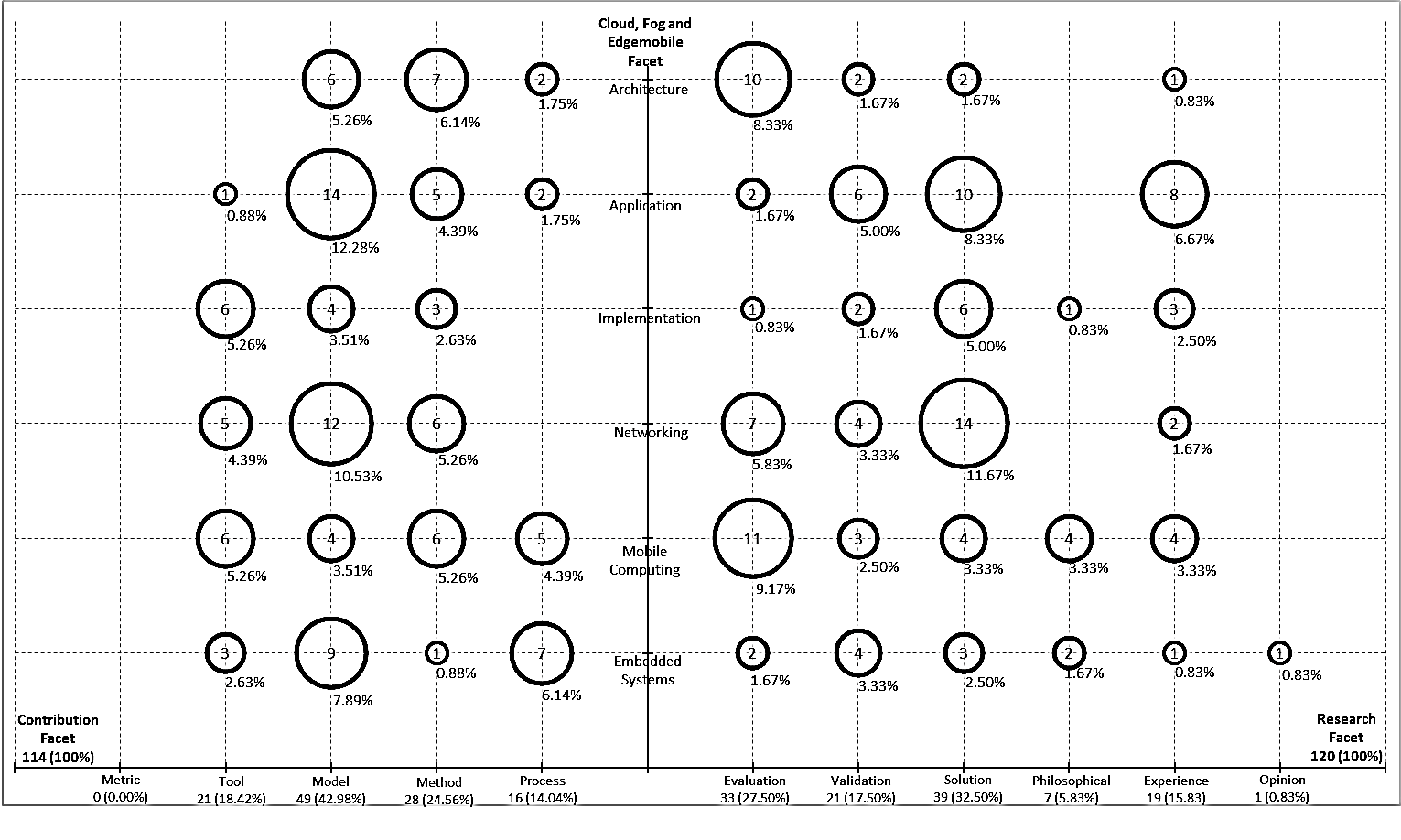 Figure 2: Systematic map of cloud fog, and edge/mobile devices management, hierarchy and business models
Figure 2: Systematic map of cloud fog, and edge/mobile devices management, hierarchy and business models
|
Table 3: Primary studies for topic and contribution facet
|
|
Table 4: Primary studies for topic and research facets
|
in terms of model, embedded systems were the least having, 0.88%, 3.51%, 0.88% and 1.75% respectively.
- In terms of the topic and research types, implementation topic in relation to evaluation research, implementation and architecture in relation to solution proposals, implementation with respect to philosophical paper, architecture and embedded systems in terms of experience papers had the least publications with 0.83%, 1.67%, 0.83% and 0.83% respectively.
From the foregoing, the visual appeal of a systematic map assists in summarizing and offering researchers with the likelihood of stimulating interest in the results.
The different categories combined together makes the bubble plot more useful. It is imperative to state that the creation of a systematic map in the absence of a successive systematic review is valuable in itself. This is because the systematic map enables the identification of research gaps and shortage of publication in this field of study. This paper provided six classes of studies namely architecture, application, implementation, networking, mobile computing and embedded systems, which could be discussed as regards to either tool, model, method, metric and process or evaluation, validation, solution, philosophical and opinion research. The few aforementioned areas, along these lines, are suggested for additional research, and the rundown of primary studies would likewise help meaning researchers.
5. Conclusion
Cloud computing is providing opportunities in different areas of human life. More areas of cloud research are opening up on a regular basis. This has led to increasing studies and consequent publications in cloud computing. There are volumes of research effort that is useful both to the cloud users and cloud providers alike. The aspect of devices management and models in relation to cloud, fog, edge and mobile computing has continued to receive attention. Despite the large quantity of publications in this field of study, the systematic map has shown that there are shortage of publications in this field of study. The visual representation provided by the systematic map enhances decision on areas of further research. This systematic mapping study has been able to identify some areas where there were less emphasis on the topic, based on the categories used in the scheme. This paper has therefore contributed to knowledge by highlighting the different aspects of the study with gaps, and recommending them for further studies. Also, further research could be carried out to validate this study or resolve contradictory issues. In summary, this study created a systematic map that could be advantageous to the cloud community, and will assist researchers in uncovering the critical gaps that were not previously explored.
Conflict of Interest
The authors declare no conflict of interest.
Acknowledgment
We acknowledge the support and sponsorship provided by Covenant University through the Centre for Research, Innovation, and Discovery (CUCRID).
Appendix: List of primary studies
- Al-Jaroodi, J., Mohamed, N., Jawhar, I., Mahmoud, S. CoTWare: A Cloud of Things Middleware (2017) Proceedings – IEEE 37th International Conference on Distributed Computing Systems Workshops, ICDCSW 2017, art. no. 7979819, pp. 214-219.
- Al-Joboury, I.M., Al-Hemiary, E.H. F2CDM: Internet of things for healthcare network based fog-to-cloud and data-in-motion using MQTT protocol (2017) Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 10542 LNCS, pp. 368-379.
- Alonso-Monsalve, S., García-Carballeira, F., Calderón, A. A heterogeneous mobile cloud computing model for hybrid clouds (2018) Future Generation Computer Systems, . Article in Press.
- Alsaffar, A.A., Pham, H.P., Hong, C.-S., Huh, E.-N., Aazam, M. An Architecture of IoT Service Delegation and Resource Allocation Based on Collaboration between Fog and Cloud Computing (2016) Mobile Information Systems, 2016, art. no. 6123234, .
- Anantula, P.R., Someswar, G.M. Protecting data in cloud environment from intruders using fog computing mechanism and control flows (2018) Proceedings of the 2nd International Conference on Communication and Electronics Systems, ICCES 2017, 2018-January, pp. 176-182.
- Arfat, Y., Aqib, M., Mehmood, R., Albeshri, A., Katib, I., Albogami, N., Alzahrani, A. Enabling Smarter Societies through Mobile Big Data Fogs and Clouds (2017) Procedia Computer Science, 109, pp. 1128-1133.
- Arun, S.H., Sharma, S.K., Chaurasia, S., Kumar, R. Detection and analysis of fog/low cloud using Ceilometer and INSAT-3D satellite data over Delhi Earth Station, New Delhi (2017) 38th Asian Conference on Remote Sensing – Space Applications: Touching Human Lives, ACRS 2017, 2017-October, .
- Bhatia, M., Sood, S.K. Exploring Temporal Analytics in Fog-Cloud Architecture for Smart Office HealthCare (2018) Mobile Networks and Applications, pp. 1-19. Article in Press.
- Bruschi, R., Davoli, F., Lago, P., Lombardo, A., Lombardo, C., Rametta, C., Schembra, G. An SDN/NFV platform for personal cloud services (2017) IEEE Transactions on Network and Service Management, 14 (4), pp. 1143-1156.
- Bruschi, R., Lago, P., Lombardo, C. In-Network Programmability for Next-generation Personal Cloud Service Support (INPUT) (2016) Procedia Computer Science, 97, pp. 114-117.
- Byrne, J., Svorobej, S., Giannoutakis, K.M., Tzovaras, D., Byrne, P.J., Östberg, P.-O., Gourinovitch, A., Lynn, T. A review of cloud computing simulation platforms & related environments (2017) CLOSER 2017 – Proceedings of the 7th International Conference on Cloud Computing and Services Science, pp. 651-663.
- Chaudhary, D., Bhushan, K., Gupta, B.B. Survey on DDoS attacks and defense mechanisms in cloud and fog computing (2018) International Journal of E-Services and Mobile Applications, 10 (3), pp. 61-83.
- Chaudhary, R., Kumar, N., Zeadally, S. Network Service Chaining in Fog and Cloud Computing for the 5G Environment: Data Management and Security Challenges (2017) IEEE Communications Magazine, 55 (11), art. no. 8114560, pp. 114-122.
- Chen, F., Li, H., Liu, J., Li, B., Xu, K., Hu, Y. Migrating big video data to cloud: a peer-assisted approach for VoD (2017) Peer-to-Peer Networking and Applications, pp. 1-15. Article in Press.
- Deepali, Bhushan, K. DDoS attack defense framework for cloud using fog computing (2018) RTEICT 2017 – 2nd IEEE International Conference on Recent Trends in Electronics, Information and Communication Technology, Proceedings, 2018-January, pp. 534-538.
- Deng, R., Lu, R., Lai, C., Luan, T.H., Liang, H. Optimal Workload Allocation in Fog-Cloud Computing Toward Balanced Delay and Power Consumption (2016) IEEE Internet of Things Journal, 3 (6), art. no. 7467406, pp. 1171-1181.
- Desirena Lopez, H.J., Siller, M., Huerta, I. Internet of vehicles: Cloud and fog computing approaches (2017) Proceedings – 2017 IEEE International Conference on Service Operations and Logistics, and Informatics, SOLI 2017, 2017-January, pp. 211-216.
- Dixit, A., Yadav, A.K., Kumar, S. An efficient architecture and algorithm for server provisioning in Cloud computing using clustering approach (2017) Proceedings of the 5th International Conference on System Modeling and Advancement in Research Trends, SMART 2016, art. no. 7894532, pp. 260-266.
- Elkhatib, Y., Porter, B., Ribeiro, H.B., Zhani, M.F., Qadir, J., Riviere, E. On using micro-clouds to deliver the fog (2017) IEEE Internet Computing, 21 (2), art. no. 7867723, pp. 8-15.
- El-Latif, A.A.A., Abd-El-Atty, B., Hossain, M.S., Elmougy, S., Ghoneim, A. Secure quantum steganography protocol for fog cloud internet of things (2018) IEEE Access, 6, pp. 10332-10340.
- Elmisery, A.M., Rho, S., Aborizka, M. A new computing environment for collective privacy protection from constrained healthcare devices to IoT cloud services (2017) Cluster Computing, pp. 1-28. Article in Press.
- Elmisery, A.M., Sertovic, M. Privacy enhanced cloud-based recommendation service for implicit discovery of relevant support groups in healthcare social networks (2017) International Journal of Grid and High Performance Computing, 9 (1), pp. 75-91.
- Elmroth, E., Leitner, P., Schulte, S., Venugopal, S. Connecting Fog and Cloud Computing (2017) IEEE Cloud Computing, 4 (2), art. no. 7912269, pp. 22-25.
- Escamilla-Ambrosio, P.J., Rodríguez-Mota, A., Aguirre-Anaya, E., Acosta-Bermejo, R., Salinas-Rosales, M. Distributing computing in the internet of things: Cloud, fog and edge computing overview (2018) Studies in Computational Intelligence, 731, pp. 87-115.
- Farris, I., Militano, L., Nitti, M., Atzori, L., Iera, A. MIFaaS: A Mobile-IoT-Federation-as-a-Service Model for dynamic cooperation of IoT Cloud Providers (2017) Future Generation Computer Systems, 70, pp. 126-137.
- Farris, I., Girau, R., Militano, L., Nitti, M., Atzori, L., Iera, A., Morabito, G. Social Virtual Objects in the Edge Cloud (2015) IEEE Cloud Computing, 2 (6), art. no. 7397053, pp. 20-28.
- Farris, I., Militano, L., Nitti, M., Atzori, L., Iera, A. Federated edge-assisted mobile clouds for service provisioning in heterogeneous IoT environments (2015) IEEE World Forum on Internet of Things, WF-IoT 2015 – Proceedings, art. no. 7389120, pp. 591-596.
- Fernandez, E.B., Yoshioka, N., Washizaki, H., Syed, M.H. Modeling and security in cloud ecosystems (2016) Future Internet, 8 (2), art. no. 13, .
- Goleva, R., Stainov, R., Kletnikov, N., Achkoski, J., Mirtchev, S., Ganchev, I., Savov, A. Performance Analysis of End-to-End Sensor-to-Cloud Personal Living Platform (2017) Procedia Computer Science, 113, pp. 615-620.
- Gupta, R., Garg, R. Mobile Applications Modelling and Security Handling in Cloud-Centric Internet of Things (2015) Proceedings – 2015 2nd IEEE International Conference on Advances in Computing and Communication Engineering, ICACCE 2015, art. no. 7306695, pp. 285-290.
- Hajibaba, M., Gorgin, S. A review on modern distributed computing paradigms: Cloud computing, jungle computing and fog computing (2014) Journal of Computing and Information Technology, 22 (2), pp. 69-84.
- Hajji, W., Tso, F.P. Understanding the performance of low power raspberry pi cloud for big data (2016) Electronics (Switzerland), 5 (2), art. no. 29, .
- Hani, Q.B., Ditcher, J.P. Stand-Out Segmentation Access Control for Cloud Outsourced Data (2017) Proceedings – 2017 IEEE 1st International Conference on Edge Computing, EDGE 2017, art. no. 8029278, pp. 210-215.
- Hasan, R., Hossain, M., Khan, R. Aura: An incentive-driven ad-hoc IoT cloud framework for proximal mobile computation offloading (2017) Future Generation Computer Systems, . Article in Press.
- Hong, H.-J. From cloud computing to fog computing: Unleash the power of edge and end devices (2017) Proceedings of the International Conference on Cloud Computing Technology and Science, CloudCom, 2017-December, pp. 331-334.
- Huang, C.-Y., Xu, K. Reliable realtime streaming in vehicular cloud-fog computing networks (2016) 2016 IEEE/CIC International Conference on Communications in China, ICCC 2016, art. no. 7636838, .
- Hung, S.-C., Hsu, H., Lien, S.-Y., Chen, K.-C. Architecture harmonization between cloud radio access networks and fog networks (2015) IEEE Access, 3, art. no. 07359093, pp. 3019-3034.
- Jalali, F., Hinton, K., Ayre, R., Alpcan, T., Tucker, R.S. Fog computing may help to save energy in cloud computing (2016) IEEE Journal on Selected Areas in Communications, 34 (5), art. no. 7439752, pp. 1728-1739.
- Jayalath, C., Stephen, J.J., Eugster, P. Atmosphere: A universal cross-cloud communication infrastructure (2013) Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 8275 LNCS, pp. 163-182.
- Kanapram, D., Lamanna, G., Repetto, M. Exploring the trade-off between performance and energy consumption in cloud infrastructures (2017) 2017 2nd International Conference on Fog and Mobile Edge Computing, FMEC 2017, art. no. 7946418, pp. 121-126.
- Khalid, A., Shahbaz, M. Adaptive deadline-aware scheme (ADAS) for data migration between cloud and fog layers (2018) KSII Transactions on Internet and Information Systems, 12 (3), pp. 1002-1015.
- Khalid, A., Shahbaz, M. Service architecture models for fog computing: A remedy for latency issues in data access from clouds (2017) KSII Transactions on Internet and Information Systems, 11 (5), pp. 2310-2345.
- Kim, O.T.T., Dang Tri, N., Nguyen, V.D., Tran, N.H., Hong, C.S. A shared parking model in vehicular network using fog and cloud environment (2015) 17th Asia-Pacific Network Operations and Management Symposium: Managing a Very Connected World, APNOMS 2015, art. no. 7275447, pp. 321-326.
- Kirkham, T., Armstrong, D., Djemame, K., Jiang, M. Risk driven Smart Home resource management using cloud services (2014) Future Generation Computer Systems, 38, pp. 13-22.
- Kirkman, S.S., Newman, R. Bridging the Cloud Trust Gap: Using ORCON Policy to Manage Consumer Trust between Different Clouds (2017) Proceedings – 2017 IEEE 1st International Conference on Edge Computing, EDGE 2017, art. no. 8029260, pp. 82-89.
- Kitanov, S., Janevski, T. Energy efficiency of 5G mobile networks in hybrid Fog and Cloud Computing environment (2016) CEUR Workshop Proceedings, 1746, pp. 41-46.
- Krishnan, Y.N., Bhagwat, C.N., Utpat, A.P. Fog computing – Network based cloud computing (2015) 2nd International Conference on Electronics and Communication Systems, ICECS 2015, art. no. 7124902, pp. 250-251.
- Kumar, R., Rajalakshmi, S. Mobile cloud computing: Standard approach to protecting and securing of mobile cloud ecosystems Computer Sciences and Applications, CSA 2013, art. no. 6835687, pp. 663-669.
- Liang, Y., Wang, T., Bhuiyan, M.Z.A., Liu, A. Research on coupling reliability problem in sensor-cloud system (2017) Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 10658 LNCS, pp. 468-478.
- Lin, Y., Shen, H. CloudFog: Leveraging Fog to Extend Cloud Gaming for Thin-Client MMOG with High Quality of Service (2017) IEEE Transactions on Parallel and Distributed Systems, 28 (2), art. no. 7465785, pp. 431-445.
- Lin, Y., Shen, H. Cloud fog: Towards high quality of experience in cloud gaming (2015) Proceedings of the International Conference on Parallel Processing, 2015-December, art. no. 7349605, pp. 500-509.
- Lin, Y., Shen, H. Leveraging Fog to Extend Cloud Gaming for Thin-Client MMOG with High Quality of Experience (2015) Proceedings – International Conference on Distributed Computing Systems, 2015-July, art. no. 7164961, pp. 734-735.
- Lobo, F.L., Lima, M., Oliveira, H., Harrington, J., El-Khatib, K. SoLVE: A localization system framework for VANets using the cloud and fog computing (2017) DIVANet 2017 – Proceedings of the 6th ACM Symposium on Development and Analysis of Intelligent Vehicular Networks and Applications, Co-located with MSWiM 2017, pp. 17-22.
- Lubamba, C., Bagula, A. Cyber-healthcare cloud computing interoperability using the HL7-CDA standard (2017) Proceedings – IEEE Symposium on Computers and Communications, art. no. 8024513, pp. 105-110.
- Macías-Macías, M., García-Orellana, C.J., González-Velasco, H., Gallardo-Caballero, R. Independent component analysis for cloud screening of meteosat images (2003) Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 2687, pp. 551-558.
- Macías-Macías, M., García-Orellana, C.J., González-Velasco, H.M., Gallardo-Caballero, R., Serrano-Pérez, A. A comparison of PCA and GA selected features for cloud field classification (2002) Lecture Notes in Artificial Intelligence (Subseries of Lecture Notes in Computer Science), 2527, pp. 42-49.
- Mahmoud, M.M.E., Rodrigues, J.J.P.C., Saleem, K., Al-Muhtadi, J., Kumar, N., Korotaev, V. Towards energy-aware fog-enabled cloud of things for healthcare (2018) Computers and Electrical Engineering, 67, pp. 58-69.
- Makitalo, N., Ometov, A., Kannisto, J., Andreev, S., Koucheryavy, Y., Mikkonen, T. Safe and Secure Execution at the Network Edge: A Framework for Coordinating Cloud, Fog, and Edge (2018) IEEE Software, . Article in Press.
- Manasrah, A.M., Aldomi, A., Gupta, B.B. An optimized service broker routing policy based on differential evolution algorithm in fog/cloud environment (2017) Cluster Computing, pp. 1-15. Article in Press.
- Masip-Bruin, X., Marin-Tordera, E., Jukan, A., Ren, G.-J. Managing resources continuity from the edge to the cloud: Architecture and performance (2018) Future Generation Computer Systems, 79, pp. 777-785.
- Masip-Bruin, X., Marin-Tordera, E., Gomez, A., Barbosa, V., Alonso, A. Will it be cloud or will it be fog? F2C, A novel flagship computing paradigm for highly demanding services (2017) FTC 2016 – Proceedings of Future Technologies Conference, art. no. 7821744, pp. 1129-1136.
- Meng, X., Wang, W., Zhang, Z. Delay-Constrained Hybrid Computation Offloading with Cloud and Fog Computing (2017) IEEE Access, 5, art. no. 8023966, pp. 21355-21367.
- Mo, Y., Peng, M., Xiang, H., Sun, Y., Ji, X. Resource allocation in cloud radio access networks with device-to-device communications (2017) IEEE Access, 5, art. no. 7855644, pp. 1250-1262.
- Mohamed, N., Al-Jaroodi, J., Jawhar, I., Lazarova-Molnar, S., Mahmoud, S. SmartCityWare: A service-oriented middleware for cloud and fog enabled smart city services (2017) IEEE Access, 5, art. no. 7990214, pp. 17576-17588.
- Mohamed, N., Lazarova-Molnar, S., Jawhar, I., Al-Jaroodi, J. Towards Service-Oriented Middleware for Fog and Cloud Integrated Cyber Physical Systems (2017) Proceedings – IEEE 37th International Conference on Distributed Computing Systems Workshops, ICDCSW 2017, art. no. 7979797, pp. 67-74.
- Mohamed, N., Lazarova-Molnar, S., Al-Jaroodi, J. Cloud of things: Optimizing smart city services (2017) 2017 7th International Conference on Modeling, Simulation, and Applied Optimization, ICMSAO 2017, art. no. 7934875, .
- Mohan, N., Zhou, P., Govindaraj, K., Kangasharju, J. Managing data in computational edge clouds (2017) MECOMM 2017 – Proceedings of the 2017 Workshop on Mobile Edge Communications, Part of SIGCOMM 2017, pp. 19-24.
- Mohan, N., Kangasharju, J. Edge-Fog cloud: A distributed cloud for Internet of Things computations (2017) 2016 Cloudification of the Internet of Things, CIoT 2016, art. no. 7872914, .
- Mueller, H., Gogouvitis, S.V., Seitz, A., Bruegge, B. Seamless computing for industrial systems spanning cloud and edge (2017) Proceedings – 2017 International Conference on High Performance Computing and Simulation, HPCS 2017, art. no. 8035079, pp. 209-216.
- Mueller, H., Gogouvitis, S.V., Haitof, H., Seitz, A., Bruegge, B. Poster abstract: Continuous computing from cloud to edge (2016) Proceedings – 1st IEEE/ACM Symposium on Edge Computing, SEC 2016, art. no. 7774685, pp. 97-98.
- Munir, A., Kansakar, P., Khan, S.U. IFCIoT: Integrated Fog Cloud IoT: A novel architectural paradigm for the future Internet of Things (2017) IEEE Consumer Electronics Magazine, 6 (3), art. no. 7948854, pp. 74-82.
- Nan, Y., Li, W., Bao, W., Delicato, F.C., Pires, P.F., Zomaya, A.Y. A dynamic tradeoff data processing framework for delay-sensitive applications in Cloud of Things systems (2018) Journal of Parallel and Distributed Computing, 112, pp. 53-66.
- Nan, Y., Li, W., Bao, W., Delicato, F.C., Pires, P.F., Dou, Y., Zomaya, A.Y. Adaptive Energy-Aware Computation Offloading for Cloud of Things Systems (2017) IEEE Access, 5, art. no. 8081765, pp. 23947-23957.
- Okafor, K.C., Ugwoke, F.N., Obayi, A.A. Evaluation of virtualized osmotic cloud network using discrete event Branch-And-Bound heuristics (2018) 2017 IEEE 3rd International Conference on Electro-Technology for National Development, NIGERCON 2017, 2018-January, pp. 425-437.
- Osanaiye, O., Chen, S., Yan, Z., Lu, R., Choo, K.-K.R., Dlodlo, M. From Cloud to Fog Computing: A Review and a Conceptual Live VM Migration Framework (2017) IEEE Access, 5, art. no. 7896564, pp. 8284-8300.
- Ostberg, P.-O., Byrne, J., Casari, P., Eardley, P., Anta, A.F., Forsman, J., Kennedy, J., Le Duc, T., Marino, M.N., Loomba, R., Pena, M.A.L., Veiga, J.L., Lynn, T., Mancuso, V., Svorobej, S., Torneus, A., Wesner, S., Willis, P., Domaschka, J. Reliable capacity provisioning for distributed cloud/edge/fog computing applications (2017) EuCNC 2017 – European Conference on Networks and Communications, art. no. 7980667, .
- Pahl, C., Helmer, S., Miori, L., Sanin, J., Lee, B. A container-based edge cloud PaaS architecture based on raspberry Pi clusters (2016) Proceedings – 2016 4th International Conference on Future Internet of Things and Cloud Workshops, W-FiCloud 2016, art. no. 7592710, pp. 117-124.
- Pham, X.-Q., Man, N.D., Tri, N.D.T., Thai, N.Q., Huh, E.-N. A cost- and performance-effective approach for task scheduling based on collaboration between cloud and fog computing (2017) International Journal of Distributed Sensor Networks, 13 (11), .
- Pradilla, J.V., Palau, C.E. Micro Virtual Machines (MicroVMs) for Cloud-assisted Cyber-Physical Systems (CPS) (2016) Internet of Things: Principles and Paradigms, pp. 125-142.
- Ramirez, W., Masip-Bruin, X., Marin-Tordera, E., Souza, V.B.C., Jukan, A., Ren, G.-J., Gonzalez de Dios, O. Evaluating the benefits of combined and continuous Fog-to-Cloud architectures (2017) Computer Communications, 113, pp. 43-52.
- Renner, T., Kliem, A., Kao, O. The Device Cloud – Applying Cloud Computing Concepts to the Internet of Things (2014) Proceedings – 2014 IEEE International Conference on Ubiquitous Intelligence and Computing, 2014 IEEE International Conference on Autonomic and Trusted Computing, 2014 IEEE International Conference on Scalable Computing and Communications and Associated Symposia/Workshops, UIC-ATC-ScalCom 2014, art. no. 7306981, pp. 396-401.
- Seo, D.B., Jeon, Y.-B., Lee, S.-H., Lee, K.-H. Cloud computing for ubiquitous computing on M2M and IoT environment mobile application (2016) Cluster Computing, 19 (2), pp. 1001-1013.
- Shah-Mansouri, H., Wong, V.W.S. Hierarchical Fog-Cloud Computing for IoT Systems: A Computation Offloading Game (2018) IEEE Internet of Things Journal, . Article in Press.
- Sharma, P.K., Chen, M.-Y., Park, J.H. A Software Defined Fog Node Based Distributed Blockchain Cloud Architecture for IoT (2018) IEEE Access, 6, art. no. 8053750, pp. 115-124.
- Sharma, S.K., Wang, X. Live Data Analytics with Collaborative Edge and Cloud Processing in Wireless IoT Networks (2017) IEEE Access, 5, art. no. 7882669, pp. 4621-4635.
- Shekhar, S., Gokhale, A. Dynamic resource management across cloud-edge resources for performance-sensitive applications (2017) Proceedings – 2017 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, CCGRID 2017, art. no. 7973763, pp. 707-710.
- Shekhar, S., Gokhale, A. Poster abstract: Enabling IoT applications via dynamic cloud-edge resource management (2017) Proceedings – 2017 IEEE/ACM 2nd International Conference on Internet-of-Things Design and Implementation, IoTDI 2017 (part of CPS Week), pp. 331-332.
- Shen, S., Huang, L., Zhou, H., Yu, S., Fan, E., Cao, Q. Multistage Signaling Game-Based Optimal Detection Strategies for Suppressing Malware Diffusion in Fog-Cloud-Based IoT Networks (2018) IEEE Internet of Things Journal, 5 (2), pp. 1043-1054.
- Shirazi, S.N., Gouglidis, A., Farshad, A., Hutchison, D. The extended cloud: Review and analysis of mobile edge computing and fog from a security and resilience perspective (2017) IEEE Journal on Selected Areas in Communications, 35 (11), art. no. 8060526, pp. 2586-2595.
- Shroff, G.Enterprise cloud computing: Technology, architecture, applications (2010) Enterprise Cloud Computing: Technology, Architecture, Applications, 9780521760959, pp. 1-273.
- Simonet, A., Lebre, A., Orgerie, A.-C. Deploying distributed cloud infrastructures: Who and at what cost? (2016) Proceedings – 2016 IEEE International Conference on Cloud Engineering Workshops, IC2EW 2016, art. no. 7527837, pp. 178-183.
- Sinaeepourfard, A., Garcia, J., Masip-Bruin, X., Marin-Tordera, E. A Novel Architecture for Efficient Fog to Cloud Data Management in Smart Cities (2017) Proceedings – International Conference on Distributed Computing Systems, art. no. 7980258, pp. 2622-2623.
- Singh, H., Bonev, B., Petkov, P., Patil, S. Cloud attenuation model at millimeter frequency bands (2018) 2017 International Conference on Infocom Technologies and Unmanned Systems: Trends and Future Directions, ICTUS 2017, 2018-January, pp. 175-180.
- Siravenha, A.C., Sousa, D., Bispo, A., Pelaes, E. Evaluating inpainting methods to the satellite images clouds and shadows removing (2011) Communications in Computer and Information Science, 260 CCIS, pp. 56-65.
- Souza, V.B., Masip-Bruin, X., Marín-Tordera, E., Sànchez-López, S., Garcia, J., Ren, G.J., Jukan, A., Juan Ferrer, A. Towards a proper service placement in combined Fog-to-Cloud (F2C) architectures (2018) Future Generation Computer Systems, 87, pp. 1-15.
- Souza, V.B., Masip-Bruin, X., Marin-Tordera, E., Ramirez, W., Sanchez-Lopez, S. Proactive vs reactive failure recovery assessment in combined Fog-to-Cloud (F2C) systems (2017) IEEE International Workshop on Computer Aided Modeling and Design of Communication Links and Networks, CAMAD, 2017-June, art. no. 8031528,
- Souza, V.B.C., Ramirez, W., Masip-Bruin, X., Marin-Tordera, E., Ren, G., Tashakor, G. Handling service allocation in combined Fog-cloud scenarios (2016) 2016 IEEE International Conference on Communications, ICC 2016, art. no. 7511465, .
- Srinivas, K.K., Ramana, T.V. Severe cause of cloud attenuation and rain attenuation on space communication link at millimetre band and differentiation between rain attenuation and cloud attenuation (2017) Proceedings – 7th IEEE International Advanced Computing Conference, IACC 2017, art. no. 7976797, pp. 255-259.
- Stankova, E.N., Korkhov, V.V., Kulabukhova, N.V., Vasilenko, A.Y., Holod, I.I. Computational environment for numerical modeling of the results of cloud seeding (2016) Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 9788, pp. 454-462.
- Syed, M.H., Fernandez, E.B. Cloud ecosystems support for internet of things and DevOps using patterns (2016) Proceedings – 2016 IEEE 1st International Conference on Internet-of-Things Design and Implementation, IoTDI 2016, art. no. 7471379, pp. 301-304.
- Taherkordi, A., Eliassen, F. Poster abstract: Data-centric IoT services provisioning in Fog-Cloud computing systems (2017) Proceedings – 2017 IEEE/ACM 2nd International Conference on Internet-of-Things Design and Implementation, IoTDI 2017 (part of CPS Week), pp. 317-318.
- Tang, C., Wei, X., Xiao, S., Chen, W., Fang, W., Zhang, W., Hao, M. A Mobile Cloud Based Scheduling Strategy for Industrial Internet of Things (2018) IEEE Access, 6, pp. 7262-7275.
- Tao, M., Ota, K., Dong, M. Foud: Integrating Fog and Cloud for 5G-Enabled V2G Networks (2017) IEEE Network, 31 (2), art. no. 7884943, pp. 8-13.
- Teerapittayanon, S., McDanel, B., Kung, H.T. Distributed Deep Neural Networks over the Cloud, the Edge and End Devices (2017) Proceedings – International Conference on Distributed Computing Systems, art. no. 7979979, pp. 328-339.
- Tinini, R.I., Reis, L.C.M., Batista, D.M., Figueiredo, G.B., Tornatore, M., Mukherjee, B. Optimal Placement of Virtualized BBU Processing in Hybrid Cloud-Fog RAN over TWDM-PON (2018) 2017 IEEE Global Communications Conference, GLOBECOM 2017 – Proceedings, 2018-January, pp. 1-6.
- Truong, H.-L., Narendra, N.C., Lin, K.-J. Notes on ensembles of IoT, network functions and clouds for service-oriented computing and applications (2018) Service Oriented Computing and Applications, 12 (1), .
- Tseng, F.-H., Cho, H.-H., Chang, K.-D., Li, J.-C., Shih, T.K. Application-oriented offloading in heterogeneous networks for mobile cloud computing (2018) Enterprise Information Systems, 12 (4), pp. 398-413.
- Van Kempen, A., Crivat, T., Trubert, B., Roy, D., Pierre, G. MEC-ConPaaS: An Experimental Single-Board Based Mobile Edge Cloud (2017) Proceedings – 5th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering, MobileCloud 2017, art. no. 7944867, pp. 17-24.
- Varghese, B., Buyya, R. Next generation cloud computing: New trends and research directions (2018) Future Generation Computer Systems, 79, pp. 849-861.
- Wang, H., Wang, Z., Domingo-Ferrer, J. Anonymous and secure aggregation scheme in fog-based public cloud computing (2018) Future Generation Computer Systems, 78, pp. 712-719.
- Wang, J., Yang, Y., Zhang, G., Yu, S. Climatic trend of cloud amount related to the aerosol characteristics in Beijing during (2010) Acta Meteorologica Sinica, 24 (6), pp. 762-775.
- Wang, L., Xie, W., Li, L., Pei, J. A thin cloud and fog removal method for remote sensing multi-spectral images (2013) Shenzhen Daxue Xuebao (Ligong Ban)/Journal of Shenzhen University Science and Engineering, 30 (6), pp. 592-597.
- Wang, S., Urgaonkar, R., He, T., Chan, K., Zafer, M., Leung, K.K. Dynamic Service Placement for Mobile Micro-Clouds with Predicted Future Costs (2017) IEEE Transactions on Parallel and Distributed Systems, 28 (4), pp. 1002-1016.
- Wang, T., Li, Y., Chen, Y., Tian, H., Cai, Y., Jia, W., Wang, B. Fog-based evaluation approach for trustworthy communication in sensor-cloud system (2017) IEEE Communications Letters, 21 (11), art. no. 8010796, pp. 2532-2535.
- Wang, T., Zeng, J., Bhuiyan, M.Z.A., Tian, H., Cai, Y., Chen, Y., Zhong, B. Trajectory Privacy Preservation Based on a Fog Structure for Cloud Location Services (2017) IEEE Access, 5, art. no. 7918561, pp. 7692-7701.
- 2016) IEEE Workshop on Local and Metropolitan Area Networks, 2016-August, art. no. 7548853, .
- Yannuzzi, M., Milito, R., Serral-Gracia, R., Montero, D., Nemirovsky, M. Key ingredients in an IoT recipe: Fog Computing, Cloud computing, and more Fog Computing(2014) 2014 IEEE 19th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks, CAMAD 2014, art. no. 7033259, pp. 325-329.
- Zeng, J., Wang, T., Jia, W., Peng, S., Wang, G. A Survey on Sensor-Cloud (2017) Jisuanji Yanjiu yu Fazhan/Computer Research and Development, 54 (5), pp. 925-939.
- Zeng, J., Wang, T., Lai, Y., Liang, J., Chen, H. Data Delivery from WSNs to Cloud Based on a Fog Structure (2017) Proceedings – 2016 International Conference on Advanced Cloud and Big Data, CBD 2016, art. no. 7815194, pp. 104-109.
- Zhao, W., Liu, J., Hara, T. Optimal Replica Distribution in Edge-Node-Assisted Cloud-P2P Platforms for Real-Time Streaming (2018) IEEE Transactions on Vehicular Technology, . Article in Press.
- R. Buyya, J. Broberg, and A. Goscinski, “Cloud computing principles and paradigms,” John Wiley and Son, 2011, pp. 4-10.
- I. Odun-Ayo, S. Misra, N. Omoregbe, E. Onibere, Y. Bulama, and R. Damasevičius, “Cloud-based security driven human resource management system,” Frontiers in Artificial Intelligence and Applications. 295, pp. 96 – 106, 2017. doi:10.3233/978-1-61499-773-3-96
- I. Odun-Ayo, M. Ananya, F. Agono, and R. Goddy-Worlu, “Cloud computing architecture: A critical analysis,” In IEEE Proceedings of the 2018 18th International Conference on Computational Science and Its Applications (ICCSA 2018), pp. 1-7 doi: 10.1109/ICCSA.2018.8439638
- I. Odun-Ayo, B. Odede, and R. Ahuja, “Cloud applications management- Issues and developments,” Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Vol.10963, pp. 683-694, 2018, Berlin, Germany: Springer.
- I. Odun-Ayo, S. Misra, O. Abayomi-Alli, and O. Ajayi, “Cloud multi-tenancy: Issues and developments,” UCC ’17 Companion, Companion Proceedings of the10th International Conference on Utility and Cloud Computing. pp. 209 – 214, 2017.
- I. Odun-Ayo, N. Omoregbe, M. Odusami, and O. Ajayi, “Cloud ownership and reliability – Issues and developments,” Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Vol. 10658, pp. 231-240, 2017, Berlin, Germany: Springer.
- S. K. Datta and C. Bonnet, “An Edge computing Architecture integrating virtual IOT Devices,” EURECO Sophia Antipolis, France.
- T. M. Beck and M. Maier, “Mobile Edge computing challenges for future Virtual Networking Embedding Algorithms,” IARIA, 2014.
- J. Wenke and M. Jiangbo, “A Reference Model of cloud operating and open source software implementation mapping,” 18th IEEE international Work Shop on enables Technologies: Infrastructures for collaborations Enterprises, 2009.
- P. Varshney and Y. Simmhan, “Demonstrating Fog computing: Characterizing Architectures, Applications and Abstractions,” arxiv: 1702.06331v1 [cs.Dc] 21 Feb. 2017.
- G. Baranwal and D. P. Vidyarthi, “A cloud service selection model using improved ranked voting method”, Concurring and Computation: Practice and Experience,” Wileyonhinelibrary.com, 2008.
- K. Petersen, R. Feldt, S. Mujtaba and M. Matisson, “Systematic Mapping Studies In Software Engineering”, EASE’08 Proceedings of the 12th international conference on Evaluation and Assessment in Software Engineering, Italy — June 26 – 27, 2008, , pp. 68-77
- J.L. Barros-Justo, A.L. Cravero-Leal, F. B. Benitti, and R. Capilla-Sevilla, “Systematic mapping protocol: the impact of using software patterns during requirements engineering activities in real-world settings,” Cornell University Library, 2017. arXiv:1701.05747v1 [cs.SE].
- T. Kosar, S. Bohra, and M. A. Mernik, “Protocol of a systematic mapping study for domain-specific languages,” Journal of Information and Software Technology 21(C). pp. 77-91, 2016.
- V. Santos, E. F. Souza, K. R. Felizardo, and N. L. Vijaykumar, “Analyzing the Use of Concept Maps in Computer Science: A Systematic Mapping Study,” Informatics in Education, 16(2) pp. 257–288, 2017. doi:10.15388/infedu.2017.13
- M. Souza, L. Veado, R. T. Moreira, E. Figueiredo, and H. Costa, “A systematic mapping study on game-related methods for software engineering education,” Information and Software Technology 95, pp. 201-218, 2018.
- C. R. Fernandez-Blanco, F. Careri, K. Kavvadias, I. Hidalgo Gonzalez, A. Zucker, and E. Peteves, “Systematic mapping of power system models: Expert survey,” EUR 28875 EN, Publications Office of the European Union, Luxembourg, 2017, ISBN 978-92-79-76462-2, doi:10.2760/422399, JRC109123.
- M. Mernik, “Domain-specific languages: A systematic mapping study,” International Conference on Current Trends in Theory and Practice of Informatics, Lecture Notes in Computer Science, Vol. 10139, pp. 464-472, 2017, Berlin, Germany: Springer.
- C. Griffo, J. P. A. Almeida, and G. Guizzardi, “A systematic mapping of the literature on legal core ontologies,” In Brazilian Conference on Ontologies, ONTOBRAS 15, 2015, CEUR Workshop Proceedings.
- A. Ahmad, P. Brereton, and P. Andras, “A systematic mapping study of empirical studies on software cloud testing methods,” In IEEE International Conference on Software Quality, Reliability and Security Companion, pp. 555-562, 2017.
- M. Alavi, and D. E. Leidner, “Knowledge management and knowledge management systems: Conceptual foundations and research issues,” MIS Quarterly, pp. 107-136, 2001.
- S. K. Boell, and D. Cecez-Kecmanovic, “On being ‘Systematic’ in literature reviews,” In Formulating Research Methods for Information Systems, Palgrave Macmillan, London, pp. 48-78, 2015.
- P. Brereton, B. A. Kitchenham, D. Budgen, M. Turner, and M. Khalil, “Lessons from applying the systematic literature review process within the software engineering domain,” Journal of Systems and Software, vol. 80, no. 4, pp. 571-583, 2007.
- H. M. Cooper, “Scientific guidelines for conducting integrative research reviews,” Review of educational research, vol. 52, no.2, pp. 291-302, 1982.
- J. L. Galvan, and M. C. Galvan, “Writing literature reviews: A guide for students of the social and behavioral sciences,” Routledge, 2017.
- B. Kitchenham, O. P. Brereton, D. Budgen, M. Turner, J. Bailey, and S. Linkman, “Systematic literature reviews in software engineering–a systematic literature review,” Information and Software Technology, vol. 51, no. 1, pp. 7-15, 2009.
- K. Petersen, S. Vakkalanka, and L. Kuzniarz, “Guidelines for conducting systematic mapping studies in software engineering: An update,” Information and Software Technology, vol. 64, pp. 1-18, 2015.
- J. Vom Brocke, A. Simons, K. Riemer, B. Niehaves, R. Plattfaut, and A. Cleven, “Standing on the Shoulders of Giants: Challenges and Recommendations of Literature Search in Information Systems Research,” CAIS, vol. 37, no. 9, 2015
- I. Odun-Ayo, R. Goddy-Worlu, O. Ajayi and E. Grant, “A Systematic Mapping Study of High Performance Computing and the Cloud”. ARPN Journal of Engineering and Applied Sciences, vol. 13, Issue 24, pp. 9886-9700, 1 Dec 2018.
- I. Odun-Ayo, O. Ajayi, R. Goddy-Worlu and J. Yahaya, “A Systematic Mapping Study of Cloud Resources Management and Scalability in Brokering, Scheduling, Capacity Planning and Elasticity”. Asian Journal of Scientific Research, vol. 12, pp. 151-166, 2019.
- A. C. Muhammed and A. B. Muhammed, “A systematic Mapping study of software architectures for cloud based systems,” Software System section, IT University of Copenhagen, 2014.
- R. Wieringa, N. A. Maiden, N. R. Mead and C. Rolland, “Requirement engineering paper classification and evaluation criteria. A proposal and a discussion,” Requirement Engineering, vol. 11, pp. 102-107, 2006.
