Multiple Social Metrics Based Routing Protocol in Opportunistic Mobile Social Networks
Volume 4, Issue 2, Page No 176-182, 2019
Author’s Name: Halikul Lenando1, Mohamad Alrfaay2,a), Haithem Ben Chikha2
View Affiliations
1Faculty of Computer Science and Information Technology, Department of Computer Systems & Communication Technologies, Universiti Malaysia Sarawak, 94300, Malaysia
2College of Computer and Information Sciences, Computer Engineering and networks, Jouf University, 72388, Saudi Arabia
a)Author to whom correspondence should be addressed. E-mail: mhrifai@ju.edu.sa
Adv. Sci. Technol. Eng. Syst. J. 4(2), 176-182 (2019); ![]() DOI: 10.25046/aj040223
DOI: 10.25046/aj040223
Keywords: Mobile social network, Social-based routing, Social features, Similarity, Centrality, Social activeness
Export Citations
In Opportunistic Mobile social networks (OMSNs), the social characteristics and behavior of humans carrying mobile devices are exploited to improve information provision and data routing in the network. Social-based routing algorithms attempt to exploit users’ social features such as similarity, centrality and betweenness, singularly or combined, to select a suitable relay node among neighbors. However, when combining multiple social metrics to enhance routing performance in opportunistic mobile social networks, most existing algorithms ignore considering the correlation and the mutual impacts among these social metrics. In this paper, we propose a social-based routing approach called Multi Social Metrics (MSM) to enhance data routing in OMSN. In MSM, three social metrics, namely degree centrality, social similarity, and social activeness are exploited, also the mutual impacts among them are considered for performance enhancement. Using real dataset traces, simulation results show the efficiency of MSM by comparing it with other benchmark schemes. Empirical results show that MSM scheme decreases the overhead ratio and the average hop count while achieving competitive delivery ratio and average latency in OMSN.
Received: 15 February 2019, Accepted: 14 March 2019, Published Online: 25 March 2019
1. Introduction
Delay Tolerant Networks (DTN) [1] is a special subclass of Ad Hoc network where an established connection between sender and receiver prior sending data is not exist or guaranteed. The connectivity in DTN is intermittent and the links between nodes are broken frequently. Data delivery in such a network is a challengeable issue; Opportunistic networks (OppNets) is a paradigm of DTN uses store-carry-forward [2] mechanism to tackle with this challenge, where message is stored in node’s buffer and carried while moving until there is an opportunity to forward it to a candidate relay. This process continues until the delivery of the message.
The wide proliferation of mobile devices leads to the emergence of the Opportunistic Mobile Social network (OMSN). In this communication form, social properties of human beings and networking technology such as, Bluetooth and Wi-Fi are combined to enable people to share information through wireless network [3]. Because of the relative stability of social characteristics and behavior of people carrying the mobile devices compared to communication links and dynamic topologies they are exploited to make data routing in OMSN more efficient [4] [5] [6][7].
In opportunistic networking paradigm, messages are forwarded neighbors. on the basis of communication opportunity with the current So, selecting the suitable relay nodes play a key role for efficient data routing process .Social-based routing algorithms utilize social metrics deduced from the mobile users’ social relationships and interconnecting to form an effective message forwarding decision when routing data in OMSN [8]. Various Social features such as similarity, centrality, and friendship are defined and utilized in the literature to design social based routing schemes [9].
Social based routing algorithms exploit social metrics either singularly [10] [11] where one social feature such as similarity or centrality is exploited, or multiple social metrics are combined to form a utility function used to select the next relay [12]. Exploiting multiple social metrics to form the forwarding strategy is strong trend in social-based routing in OMSN. However, when exploiting multiple social metrics we believe that it is important to consider the interrelations and the mutual impacts among the exploited social features and not utilize them separately.
In this paper, we propose a social-based routing scheme that exploits multiple social properties namely, social activity, centrality, and similarity, and we also consider the mutual impacts and interrelation between these social metrics to ensure efficient forwarding decision in OMSN. The rest of the paper structure is organized as follows. In section 2, related works are discussed with motivation for our proposed scheme. Section 3 presents an overview of our proposed protocol and the social metrics that are exploited to form the forwarding decision. Experimental simulation results and performance evaluation are presented in Section 4. Section 5 concludes this paper.
2. Related works and motivation
Data routing in OMSN is one of the key challengeable issues that derive tremendous interest in the research community where several routing strategies have been proposed [2] [13] [14]. These schemes aim to tackle with the intermittent and dynamic topology of the opportunistic networks and to develop efficient routing protocols with higher delivery ratio and lower delivery overhead and end-to-end delay. Flooding and flooding-based schemes like Epidemic [15] is the straightforward routing schemes in the opportunistic networks, where replicas overwhelm the network in the sake of delivering data to destinations. However, these schemes exhaust the network and the node’s resources because of the high rate of message replication.
Prediction and probability based routing schemes like PRoPHET [16] protocol depend on the contact history between nodes to predict the future encounter. Each node calculates and maintains the encounter probability with other peers, where this probability is increased with every meeting and decreases if nodes do not meet over time. In these schemes, pervious interactions are the key factor to form the forwarding decision while other factors such as social relations and behavior patterns are not considered.
Social characteristics of mobile users and the related social properties provided by Socially Aware Networking (SNA) [17] are exploited widely in the literature to improve routing performance in OMSN [18] . The common goal of the social-based schemes is to make more accurate forwarding decision by selecting a relay which has the largest probability to encounter the destination by exploiting social properties. Different social metrics, such as similarity, activity, and popularity are defined to reflect the social relation and ties among mobile nodes [3]. These metrics are exploited to design efficient social-based routing protocols in OMSN [19] . In [10], a fuzzy routing-forwarding algorithm (FCNS) was proposed to exploit node similarity. This scheme considers the similarity among social attributes and the nodes’ mobility history, and also it uses feedback mechanism for more stable forwarding of message in the network.
Exploiting multiple social metrics such as, similarity, betweenness and popularity for efficient routing is strong trend in the research community. In Bubble Rap [20] , similarity and community structure are exploited. In this algorithm, communities with different sizes are formed. Nodes belong to these communities have different levels of ranking of two types; global denotes node’s popularity in the entire network and local for node’s popularity inside the community. A node is selected as a relay if it has higher global ranking until a node in the destination’s community is encountered. Then, local ranking is examined to forward messages to nodes that have higher local ranking until reaching the destination.
Xia et al. [12] consider multiple social characteristics to design multi-dimensional routing protocol for socially-aware networking. Three social factors are utilized in this work. The first one is physical proximity which indicates the contacting ability when two nodes within their communication rang. The second one is user interests, it reflects the users’ preferences, and finally social relationship which reflects the social ties and relationships with other peers such as friendship and family relations. Utility function is composed based on these factors and messages are forwarded to nodes that have the highest utility value when nodes encounter.
Rahim et al. [21] proposed a social-based routing protocol for data dissemination in Vehicular Social Networks (VSNs).The proposed protocol, named Social-Acquaintance based Routing Protocol (SARP), exploits multiple social metrics; community acquaintance, social activeness, and degree centrality. Each node maintains and updates the values of these metrics and a priority value is calculated based on them. When a message carrying node encounters another node, messages will be forwarded if the encountered node has higher priority value than the relay.
Social properties such as popularity, similarity and similarity describe the social behavior of a mobile user in a network, and the interactions among different users in the network and their social behaviors are interrelated. Therefore, for efficient data routing and information provision in OMSN, the correlation and the mutual impacts among the exploited social features should be considered. Therefore, unlike the other above-mentioned methods, in this paper, we propose a social based routing scheme called MSM that considers the mutual impact of the social metrics. Three social metrics namely social activity, centrality, similarity and their mutual correlations are exploited to form a utility function used for the selection of the best relay for forwarding a message in OMSN. We present the details of the proposed protocol in the next section.
3. Proposed routing protocol
MSM is a social based routing protocol. It utilizes three social metrics; social activity, social similarity, and social centrality. These three metrics are combined together in conjunction with the correlation among them in order to make more precise forwarding decision.
Social activity, similarity, and centrality are common social metrics in the Mobile Social Network (MSN) [18] [22]. In the next subsections, we define these metrics and we present the way how we evaluate them.
3.1. Social Activity
The opportunistic network has a dynamic topology, so the current neighbors of each node change frequently. Node that has higher rate of meeting new peers is considered socially active node. For example, if there are two nodes N1 and N2 , and at time t1: the neighbors of node N1 are: N2, N4, N3 and N7 , while the neighbor of node N2 are: N1, N4, N5 and N9 . Then at time t2 where t2> t1, N1 has the neighbors: N3, N4, N5 and N7, while the neighbors of N2 are: N8, N12, N6 and N9. In this example, node N2 is more socially active than node N1 because it has more new peers at t2 i.e. N8, N12 and N6, while N1 has only one new neighbor: N5.
The social activity of a node is calculated as follows [20]:
Act(Ni )=1- (Nibtl ∩ Nibtp) / (Nibtl ⋃ Nibtp) (1)
where tl represents the time of the last change in the neighbors of Ni and tp denotes the time of the previous change in the neighbors of Ni . Nibtl , Nibtp are the set of the current neighbors of Ni at tl and tp , respectively.
3.2. Social similarity
From the social science, people tend to build clusters inside their social networks with peers have common social characteristics, behaviors, or friends. People belongs to a cluster may meet each other more frequently than others, and hence the probability of the future meeting is high [3].
The similarity between two nodes Ni and Nj based on the common neighbors is computed as:
SimNbi,j = Nbi ∩ Nbj (2)
where Nbi and Nbj are the current neighbors of nodes Ni and Nj respectively [5].
3.3. Degree centrality
It is an indicator of the social importance (popularity) of a node in the social network. Node gets higher popularity when it encounters more other nodes in the network. So, the increasing in degree centrality results in higher probability to deliver messages.
Degree centrality of a node N_i calculate as follows [6] :
DC(Ni) = ∑i=1,N En (i,k) , (3)
where En (i,k) =1 if there is a direct connection between Ni and Nk. N denotes the number of the nodes in the network.
3.4. Forwarding policy
In our work, social activity, degree centrality, and social similarity are combined to make the forwarding decision when routing messages in OMSN. An encounter node will be selected as a relay in two cases: first, if it is more socially active than the current node, and it has a similarity with the destination and its similarity is more than the current relay node. We put this condition because there is a probability that a node has higher social activity (meet more new people frequently) but it is socially far from the destination. So that, forwarding message to such a node is an unwise decision. Applying this condition leads to select relays that are more socially closer to the destination and hence the probability to encounter the destination is higher. The second case; the relay has higher centrality metric than the current node and it has contacted with the destination before and if it has a similarity with the destination.
We define a utility function UNi of a node Nj as following:
UNi = SimFi,j × Act (Nj) + CenFi,j × DC(Nj) (4)
The factors SimFi,j and CenFi,j are used to strict the selection of the relay to the nodes that are socially closer to the destination. Act (Nj) is calculated based on (1) and DC(Nj) is calculated based on (3) .
According to similarity metric, a node will be selected as a relay only if it has a similarity with the destination and if it has higher similarity value than the current node. So that, the value of the similarity factor is:
SimF = 1 : ∆simi,j = SimNbj,d – SimNbi,d > 0 (5)
SimF = 0 : ∆simi,j = SimNbj,d – SimNbi,d ≤ 0 (6)
While for centrality metric the relay will be chosen only if it encountered the destination previously and it has a similarity with the destination. So, the value of the centrality factor cenF is:
cenF = 1: SimNbj,d > 0 and Encj,d ≠ 0 (7)
cenF = 0: SimNbj,d ≤ 0 or Encj,d ≠ 0 (8)
here similarities are calculated based on (2).
When a node Ni encounters another node Nj , each node calculates the values of Act (Ni), Act (Nj), SimNbi,d, SimNbj,d, , and Encj,d metrics for each message stored in their buffers. Then based on these values, each node evaluates SimF, cenF. Finally, the utility of the two nodes UNi , UNj is calculated. If and only if the utility of the encountered node UNj is greater than the current node UNi, the message will be forwarded to the encountered node, else the current node continues carrying the message.
Algorithm 1 shows the pseudo code of the forwarding process in MSM.
Algorithm 1: Pseudo-code of forwarding process in MSM
1: Nodei encounter Nodej
2: For each message in Nodei buffer
3: compute Act(Ni), Act(Nj), SimNbj,d , SimNbi,d , Enc j,d
4: Compute SimF, CenF
5: Compute UNj, UNi
6: If UNi > UNj
7: forward message to Nodej
8: End if
9: End for
Regarding the time complexity of Algorithm 1, each node computes the social metrics values for all of its buffered messages, therefore the complexity is proportional to the number of the buffered messages (M). So, the complexity of Algorithm1 is O(M).
4. Performance evaluations
4.1. Data set
Traces of real datasets are used to do our experiments and to evaluate the efficiency of MSM. INFOCOM05 and INFOCOM06 datasets were used for evaluation. These datasets is widely used in the literature [12] [23] and available at the website of CRAWDAD project (http://crawdad.org/cambridge/haggle).
INFOCOM05 dataset is conducted during the IEEE INFOCOM 2005 conference in Miami where 41 iMotes devices with wireless range of around 30 meters using Bluetooth technology for communication. The experiment where carried by attendees for 3 to 4 days. In INFOCOM06 dataset, 78 mobile iMotes are used. Bluetooth encounters between 78 short range nodes are traced and stored.
4.2. Simulation setup
We use Opportunistic Network Environment (ONE) [24] simulator to do the experiments. We compare MSM with three benchmark routing protocols: Epidemic which is flooding-based routing protocol, PRoPHET which is prediction-based routing protocol and Bubble Rap which is social-based routing protocol. Simulator settings are as follows:
The Broadcast type is Bluetooth interface with the transmit speed of 2 Mbps for all the nodes. The message event generator in ONE simulator generates one new message in every 30 to 40 seconds. Message size is 124 KB. We vary the simulation end time from 4hours (14400 seconds) to 40 hours (144000 seconds) by 4 hours step for INFOCOM06 dataset, and from 4hours (14400 seconds) to approximately 70 Hours (254150 seconds) for INFOCOM05 dataset. Also, we change message TTL value as follows: (10m, 30m, 1h, 4h, 8h, 16h, 20h, 1d, 1d&4h, 1d&8h, 1.5d, 1.6d) where m stands for minutes, h for hours and d for days.
Simulation setup settings are given in Table 1.
Table 1: Simulation Settings
| Simulation Time(seconds |
(INFOCOM05):14400 to 254150 (INFOCOM06):14400 to 144000 with 4hours step |
| Interface | Bluetooth Interface |
| Number of nodes | 41 short range devices in (INFOCOM05) 78 short range devices in (INFOCOM06) |
| Transmit Speed | 250 k (2 Mbps) |
| Mobility | Real trace data (INFOCOM05, INFOCOM06) |
| Buffer Size | 5 MB |
| Protocols | MSM, Epidemic , PRoPHET, BubbleRap |
| Message Size | 128 KB |
| Event Interval | 30 to 40 seconds |
| Message TTL | 10m, 30m, 1h, 4h, 8h, 16h, 20h, 1d, 1d&4h, 1d&8h, 1.5d, 1.6d |
In each experiment, we compare the performance of protocols MSM, Epidemic, PRoPHET and Bubble Rap based on the following metrics:
Successful Delivery ratio: it is the ratio between the number of delivered messages and the total number of created messages. The ideal value of the successful delivery ratio is (1.0) when all created messages are delivered to their destinations.
Overhead Ratio: it is the additional bytes are sent for successfully delivering a message to a destination.
Average Latency: it is the average of the time elapsed between message creation and delivery.
Average Hop Count: it is the average of the number of hops that messages must take in order to reach the destination.
4.3. Experiments and results
In this work, we carried out a comparison between the proposed MSM and Epidemic, PRoPHET and
Bubble Rap in terms of delivery ratio, overhead ratio, average latency and average hop count respectively. Figures 1, 2, 3, and 4 show the evaluation of the protocols’ performance over the experiment time for the both datasets. We aim to study the achievement of our protocol against the benchmark protocols over the time of the experiment. For this purpose, we fixed the messages TTL to 600m (10 Hours) and the buffer size to 5MB and change the simulation end time from 14400s (4 Hours) to 144000s (1.6Day) for INFOCOM06 dataset, and from 14400s (4 Hours) to 254150s (2.9 Day) for INFOCOM05 dataset with 4 Hours step.
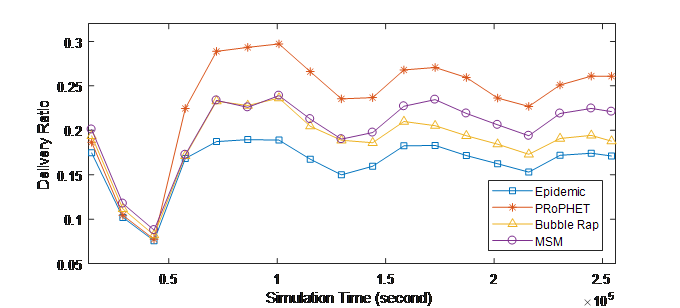 Figure 1. (a) Delivery ratio over Time (INFOCOM05)
Figure 1. (a) Delivery ratio over Time (INFOCOM05)
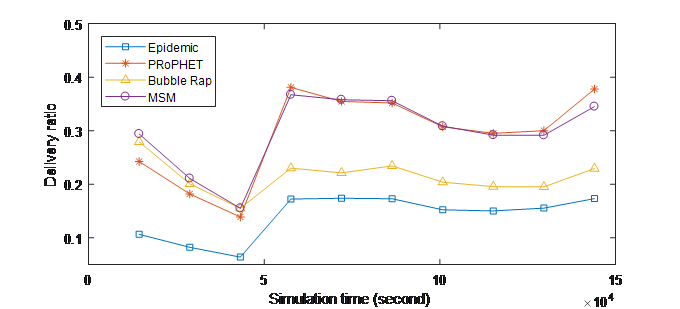 Figure 1. (b) Delivery ratio over Time (INFOCOM06)
Figure 1. (b) Delivery ratio over Time (INFOCOM06)
Figure 1 depicts the successful delivery ratio over the time. From these results, it is clearly shown that MSM outperforms both Epidemic and Bubble Rap and has close achievement compared to PRoPHET over the experiment time. This is because MSM exploits three social metrics to make forwarding decision, so it forwards messages to nodes that are socially closer to the destination. In addition, considering the correlation between the different social metrics, where social similarity adjusts social activity and similarity and contact history adjust centrality, makes the forwarding decision more accurate. Therefore, the selected relays in MSM have higher probability to encounter the destination and the delivered data amount will be higher. This results in increasing the delivery ratio in the network.
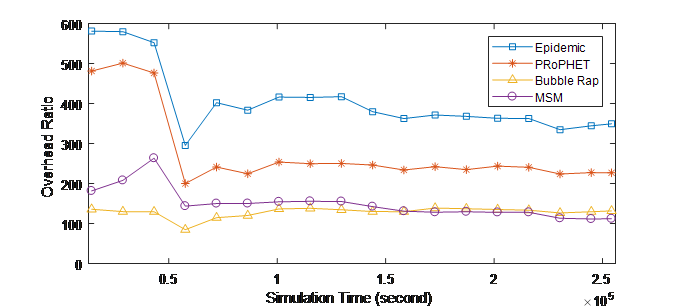 Figure 2. (a) Overhead ratio over Time (INFOCOM05)
Figure 2. (a) Overhead ratio over Time (INFOCOM05)
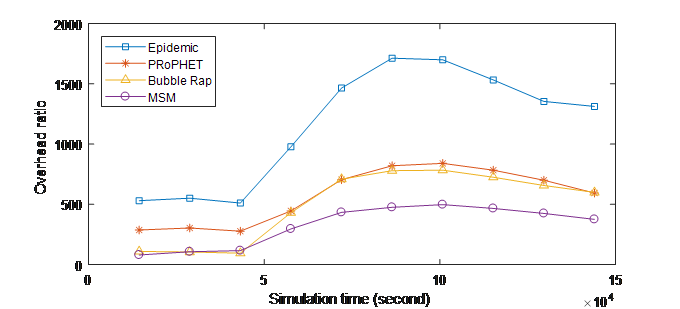 Figure 2. (b) Overhead ratio over Time (INFOCOM06)
Figure 2. (b) Overhead ratio over Time (INFOCOM06)
Figure 2 shows that MSM is able to significantly control the overhead in OMSN with high delivery rates as shown in Figure 1. MSM achieves a higher reduction in delivery overhead in INFOCOM06 experiment than INFOCOM05. This is because INFOCOM06 has higher number of mobile nodes, so the exploiting of the social information has more impact on the routing performance.
Compared to Bubble Rap, MSM has almost similar performance at the beginning of the experiment (First 8 Hours) in INFOCOM06 experiment where the overhead ratio is the lowest compared to Epidemic and PRoPHET. Then, for the proceeding in the experiment time, MSM outperforms all the other protocols with high reduction in the overhead ratio. In fact, the gain is about (36%, 39%, and 70%) by comparing with Bubble Rap, PRoPHET, and Epidemic, respectively. Gain is thanks to exploitation of social information by MSM in an effective way, i.e., social metrics including the activity, the centrality, the similarity and their mutual impacts that allow the selection of the relay, which is socially closer to the destination. This decreases the forwardings in the network while increases the delivered messages. Consequently, the overhead ratio (relayed-delivered/ delivered) will be decreased.
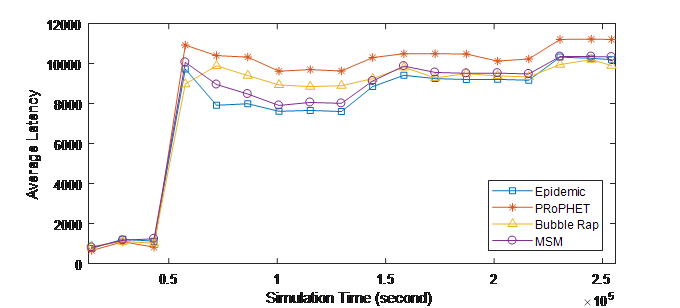 Figure 3. (a) Average latency over Time (INFOCOM05)
Figure 3. (a) Average latency over Time (INFOCOM05)
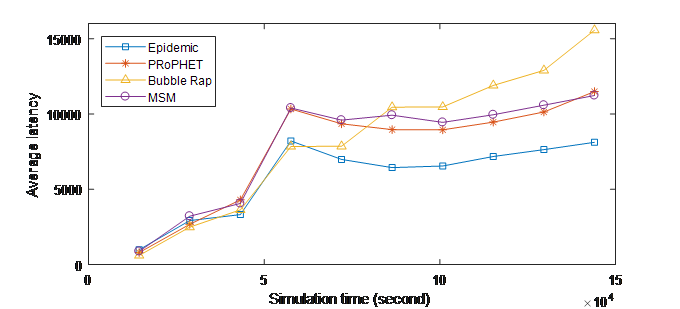 Figure 3. (b) Average latency over Time (INFOCOM06)
Figure 3. (b) Average latency over Time (INFOCOM06)
Figures 3 shows the performance evaluation in term of average latency. Epidemic has the best achievement regarding this metric because it is a flooding-based scheme. However, in INFOCOM05 experiment, MSM has, on average, lower average latency compared with Bubble Rap and PRoPHET Protocols and has very close achievement compared to Epidemic. In INFOCOM06 experiment, MSM almost has similar average latency compared to PRoPHET and it outperforms Bubble Rap at the end of the experiment.
In Figure 4, it is clear that MSM outperforms all other protocols in term of average hop counts. Exploiting three social metrics and considering the mutual impacts among them enables MSM to decrease the number of forwardings in the network. Selecting the next forwarder in MSM is based on the strength of the social relationship with the destination, so a lower number of mobile nodes will contribute in the forwarding process, this results in decreasing the average hop count and help to preserve the network and nodes resources.
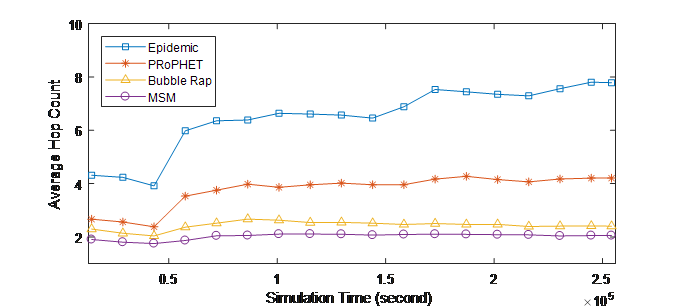 Figure 4. (a) Average hop count over Time (INFOCOM05)
Figure 4. (a) Average hop count over Time (INFOCOM05)
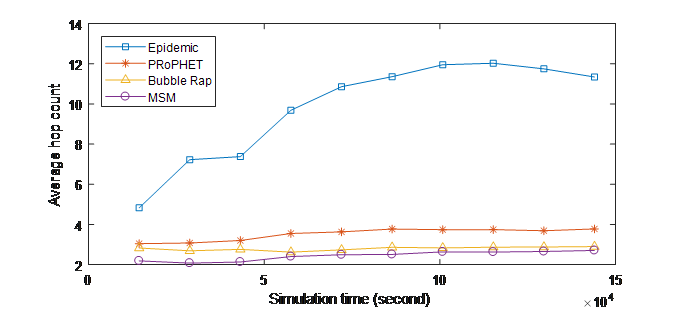 Figure 4. (b) Average hop count over Time (INFOCOM06)
Figure 4. (b) Average hop count over Time (INFOCOM06)
We also investigate the efficiency of MSM for different TTL values. In fact, we evaluate the performance by changing the TTL from value low vale 10 minutes to high value 1.6 days. In Figures 5, 6, 7 and 8, we plot the varying of delivery ratio, overhead ratio, average latency and average hop count versus TTL value for both datasets.
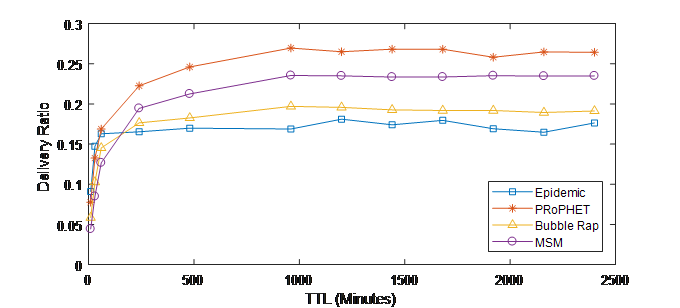 Figure 5. (a) Delivery ratio vs. TTL (INFOCOM05)
Figure 5. (a) Delivery ratio vs. TTL (INFOCOM05)
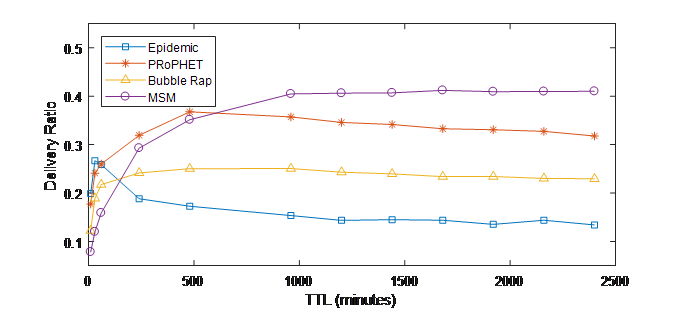 Figure 5. (b) Delivery ratio vs. TTL (INFOCOM06)
Figure 5. (b) Delivery ratio vs. TTL (INFOCOM06)
It is shown in Figure5 (a) and (b) that all routing scheme have low delivery ratio in low TTL values scenarios (10m-1h). This is due to the high dropping ratio of messages as a result of expired TTL. Increasing TTL causes rising up the delivery ratio until reach a plateau where increasing TTL values decrease slightly the delivery ratio.
For very low TTL values (i.e., 10, 30 and 60 minutes), MSM has a low number of delivered messages since it straitens the selection of relay nodes based on the social metrics. This results in a very low number of delivered messages hence low delivery ratio. However, with increasing TTL value, MSM achieves better delivery ratio and outperforms all other schemes except PRoPHET in INFOCOM05 and all other schemes INFOCOM06 when TTL is higher than 8 hours. This is because MSM forwards messages to nodes having tight social relations with destinations, which increases the probability of delivering the message.
Figure 6 shows the overhead ratio vs. the TTL value. The results show that MSM provide significant gain comparing to all other schemes and for all TTL values for both datasets. It reduces the overhead in the network by applying a strict relay selection strategy, where social activity, similarity and similarity metrics are exploited to select the next message’s forwarder. The objective of this forwarding method of MSM is to reduce the number of forwardings in the network and also forward messages to nodes that are more socially closer to the destination and therefore have a have high probability to deliver messages.
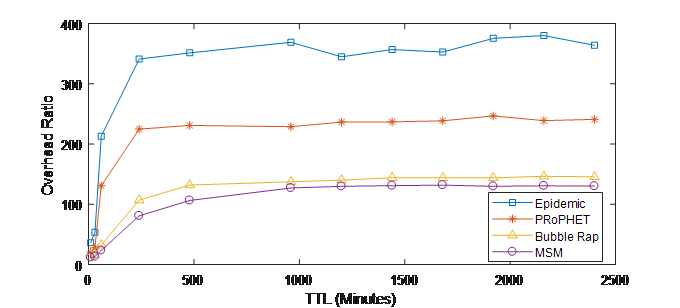 Figure 6. (a) Overhead ratio vs. TTL (INFOCOM05)
Figure 6. (a) Overhead ratio vs. TTL (INFOCOM05)
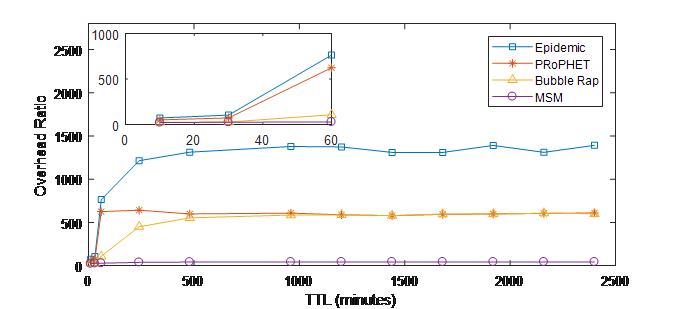 Figure 6. (b) Overhead ratio vs. TTL (INFOCOM06)
Figure 6. (b) Overhead ratio vs. TTL (INFOCOM06)
Average latency of MSM in comparison with Epidemic, PRoPHET and Bubble Rap with respect to TTL value is given in figures 7. (a) and (b). It is shown in this figure that MSM achieves a close performance compared to the other protocols and has lower average latency than PRoPHET in INFOCOM05 experiment while it outperforms both PRoPHET and Bubble Rap in INFOCOM06 and its superiority becomes higher as TTL value increases. This is because MSM selects relays that have stronger social ties with the destination, which means that they will deliver messages in a shorter end-to-end delay. Therefore, the average latency of MSM is lower. Compared to Epidemic, MSM achieves higher average latency because Epidemic is a flooding-based approach so it has the lowest end-to-end delay compared to other protocols in OMSN.
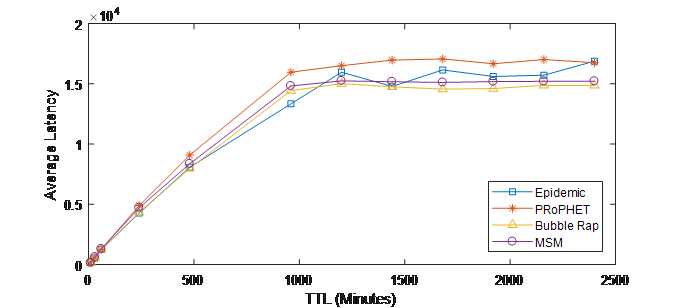 Figure 7. (a) Average latency vs. TTL (INFOCOM05)
Figure 7. (a) Average latency vs. TTL (INFOCOM05)
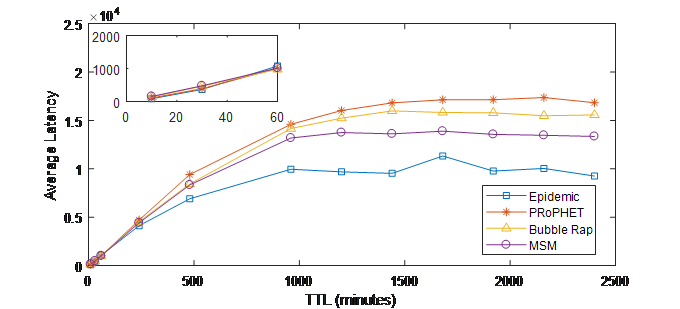 Figure 7. (b) Average latency vs. TTL (INFOCOM06)
Figure 7. (b) Average latency vs. TTL (INFOCOM06)
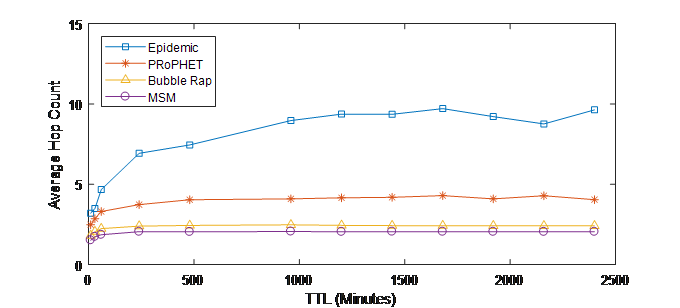 Figure 8.(a) Average hop count vs. TTL(INFOCOM05)
Figure 8.(a) Average hop count vs. TTL(INFOCOM05)
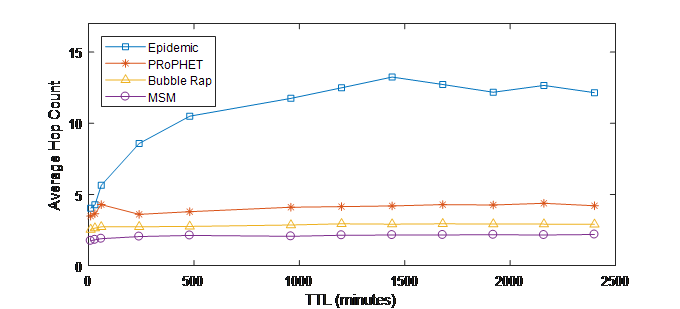 Figure 8.(b) Average hop count vs. TTL (INFOCOM06)
Figure 8.(b) Average hop count vs. TTL (INFOCOM06)
Figure 8 depicts the achievements of MSM, Epidemic, PRoPHET and Bubble Rap in term of average hop counts metric. From this results, it is clear that MSM has the lowest average hop counts, so it decreases network and node overhead in OMSN. The reason is that MSM decreases the number of nodes participating in messages forwarding by selecting as a relay only node which has better social relation with destination based on the three social metrics, i.e., activity, similarity and centrality.
5. Conclusion
In this paper, we have presented a social-based routing scheme exploiting three social metrics; activity, centrality and similarity. The protocol, namely, Multi Social Metrics routing protocol (MSM), exploit the social metrics and their mutual impacts to improve routing performance in OMSN, and precisely we focused on controlling node and network overhead in OMSN by decreasing delivery overhead and average hop counts. Real mobility traces are used to evaluate our proposal where simulation results are carried out by ONE simulator to show the efficiency of the proposed protocol. We compared MSM performance with three widely well-known routing protocols in OMSN; Epidemic, PRoPHET, and Bubble Rap. The results show that MSM outperforms theses protocols in terms of overhead ratio, average hop count and has competitive for delivery ratio and average latency. This routing scheme and its forwarding strategy can be applied in any mobile social network scenarios such as conference or university campus.
Conflict of Interest
The authors declare no conflict of interest.
- KHABBAZ, Maurice J., ASSI, Chadi M., and FAWAZ, Wissam F.,, “Disruption-tolerant networking: A comprehensive survey on recent developments and persisting challenges,” IEEE Communications Surveys & Tutorials, vol. 14, no. 2, pp. 607–640, 2012.
https://doi.org/10.1109/SURV.2011.041911.00093 - Zhu, Konglin and Li, Wenzhong and Fu, Xiaoming and Zhang, Lin, “Data routing strategies in opportunistic mobile social networks: Taxonomy and open challenges,” Computer Networks, vol. 93, pp. 183–198, 2015. https://doi.org/10.1016/j.comnet.2015.10.018
- Daly, Elizabeth M and Haahr, Mads, “Social Network Analysis for Information Flow in Disconnected Delay-Tolerant MANET” IEEE Transactions on Mobile Computing, vol. 8,no. 2, pp. 606–621, 2009.
https://doi.org/10.1109/TMC.2008.161 - Boldrini, Chiara and Conti, Marco and Passarella, Andrea, “Exploiting users’ social relations to forward data in opportunistic networks: The HiBOp solution,” Pervasive and Mobile Computing, vol. 4, no. 5, pp. 633–657, 2008.
https://doi.org/10.1016/j.pmcj.2008.04.003 - Guan, Jianfeng and Chu, Qi and You, Ilsun, “The social relationship based adaptive multi-spray-and-wait routing algorithm for disruption tolerant network,” Mobile Information Systems, vol. 2017, 2017.
https://doi.org/10.1155/2017/1819495 - Halikul Lenando and Mohamad Alrfaay, “EpSoc: Social-based epidemic-based routing protocol in opportunistic mobile social network,” Mobile Information Systems, vol. 2018, p. 8, 2018.
https://doi.org/10.1155/2018/6462826 - Wang, Tong and Tang, MengBo and Song, Houbing and Cao, Y and Khan, Zaheer, “Opportunistic protocol based on social probability and resources efficiency for the intelligent and connected transportation system,” Computer Networks, vol. 149, pp. 173–186, 2019.
https://doi.org/10.1016/j.comnet.2018.11.034 - Pirozmand, Poria and Wu, Guowei and Jedari, Behrouz and Xia, Feng, “Human mobility in opportunistic networks: Characteristics, models and prediction methods,” Journal of Network and Computer Applications, pp. 45–58, 2014.
https://doi.org/10.1016/j.jnca.2014.03.007 - Ahmed, Manzoor and Li, Yong and Waqas, Muhammad and Sheraz, Muhammad and Jin, Depeng and Han, Zhu, “A Survey on socially aware device-to-device communications,” IEEE Communications Surveys & Tutorials, vol. 20, no. 3, pp. 2169–2197, 2018.
https://doi.org/10.1109/COMST.2018.2820069 - Liu, K.; Chen, Z.; Wu, J.; Wang, L., “FCNS: A fuzzy routing-forwarding algorithm exploiting comprehensive node similarity in opportunistic social networks,” Symmetry 2018, 10, 338. https://doi.org/10.3390/sym10080338
- Asl, Sepideh Tahouri and Derakhshanfard, Nahideh, “SFQ: Social Features Based Quota Routing in Mobile Social Networks,” Wireless Personal Communications, vol. 104, no. 3, pp. 1109–1120, 2019.
https://doi.org/10.1007/s1127 - Xia, Feng and Liu, Li and Jedari, Behrouz and Das, Sajal K, “PIS: A multi-dimensional routing protocol for socially-aware networking,” IEEE Transactions on Mobile Computing, no. 11, pp. 2825–2836, 2016.
https://doi.org/10.1109/TMC.2016.2517649 - Sobin, CC and Raychoudhury, Vaskar and Marfia, Gustavo and Singla, Ankita, “A survey of routing and data dissemination in delay tolerant networks,” Journal of Network and Computer Applications, vol. 67, pp. 128–146, 2016. https://doi.org/10.1016/j.jnca.2016.01.002
- N. Chakchouk, “A survey on opportunistic routing in wireless communication networks,” IEEE Communications Surveys & Tutorials, vol. 17, no. 4, pp. 2214–2241, 2015.
https://doi.org/10.1109/COMST.2015.2411335 - Amin Vahdat , David Becker, “Epidemic Routing for Partially-Connected Ad Hoc Networks,” Duke University, Technical Report CS-200006, 2000.
- Lindgren, Anders and Doria, Avri and Schelen, Olov, “Probabilistic routing in intermittently connected networks,” Springer, pp. 239–254, 2004.
https://doi.org/10.1007/978-3-540-27767-5_24 - Xia, Feng and Liu, Li and Li, Jie and Ma, Jianhua and Vasilakos, Athanasios V, “Socially Aware Networking: A Survey,” IEEE Systems Journal, vol. 9, no. 3, pp. 904–921, 2015.
https://doi.org/10.1109/JSYST.2013.2281262 - Zhu, Ying and Xu, Bin and Shi, Xinghua and Wang, Yu, “A survey of social-based routing in delay tolerant networks: Positive and negative social effects,”
IEEE Communications Surveys & Tutorials, vol. 15, no. 1, pp. 387–401,
2013.
https://doi.org/10.1109/SURV.2012.032612.00004 - Roy, Animesh and Acharya, Tamaghna and DasBit, Sipra, “Quality of service in delay tolerant networks: A survey,” Computer Networks, vol 130, pp. 121-133, 2018.
https://doi.org/10.1016/j.comnet.2017.11.010 - Hui, Pan and Crowcroft, Jon and Yoneki, Eiko, “Bubble rap: Social-based forwarding in delay-tolerant networks,” IEEE Transactions on Mobile Computing, vol. 10, no. 11, pp. 1576-1589, 2011.
https://doi.org/10.1109/TMC.2010.246 - Rahim, Azizur and Qiu, Tie and Ning, Zhaolong and Wang, Jinzhong and Ullah, Noor and Tolba, Amr and Xia, Feng, “Social acquaintance based routing in Vehicular Social Networks,” Future Generation Computer Systems, vol. 93, pp. 751-760, 2017.
https://doi.org/10.1016/j.future.2017.07.059 - Wang, Yufeng and Vasilakos, Athanasios V and Jin, Qun and Ma, Jianhua, “Survey on mobile social networking in proximity (MSNP): approaches, challenges and architecture,” Wireless networks, vol. 20, no. 6, pp. 1295–1311, 2014.
https://doi.org/10.1007/s11276-013-0677-7 - Yao, Lin and Man, Yanmao and Huang, Zhong and Deng, Jing and Wang, Xin, “Secure routing based on social similarity in opportunistic networks,” IEEE Transactions on Wireless Communications, vol. 15, no. 1, pp. 594–605, 2016. https://doi.org/10.1109/TWC.2015.2476466
- Ari Keränen, Jörg Ott , Teemu Kärkkäinen, “The ONE simulator for DTN protocol evaluation,” in Simutools ’09 Proceedings of the 2nd International Conference on Simulation Tools and Techniques, Brussels, Belgium, 2009.
https://doi.org/10.4108/ICST.SIMUTOOLS2009.5674
