Optimized use of RFID at XYZ University Library in Doing Auto Borrowing Book by Utilizing NFC Technology on Smartphone
Volume 6, Issue 1, Page No 532-537, 2021
Author’s Name: Rony Baskoro Lukito1,a), Vilianty Rizki Utami2
View Affiliations
1Computer Science Department, Bina Nusantara University, Jakarta, 11480, Indonesia
2Department of Management, University of Indonesia, Jakarta, 11480, Indonesia
a)Author to whom correspondence should be addressed. E-mail: rblukito@gmail.com
Adv. Sci. Technol. Eng. Syst. J. 6(1), 532-537 (2021); ![]() DOI: 10.25046/aj060158
DOI: 10.25046/aj060158
Keywords: Auto Borrowing Book, library, NFC, RFID
Export Citations
NFC (Near Field Communication) is a contactless communication technology based on a radio frequency (RF) field using a base frequency of 13.56 MHz. NFC technology is perfectly designed to exchange data between two devices via simple touch gestures. RFID is the process of identifying an object directly by radio frequency. There are two important components of an RFID system is the card or label (tag) and the reader. In each of tags have unique ID. In addition to the ID, the tag also contained a block that is used for security. On the application in the library, all the books that will be read by the reader have an RFID tag in it. With the tag on each book that is used for lending service, it can be made an application on a smartphone that supports NFC (Near Field Communication) which can be used by each user to borrow books independently, that does not need to come to the library staff to borrow books.
Received: 16 December 2020, Accepted: 10 January 2021, Published Online: 28 January 2021
1. Introduction
With the development of ICT (Information and Communication Technology) by leaps and bounds, ICT can be applied to almost all existing activities, including at the university. One is the use of RFID on all student, lecturer and staff cards. So with RFID card, students and faculty can record the lecture attendance, borrow books, pay to eat, with just to put the RFID card on a card reader.
The library is one of the institutions that uses ICT to optimize its management which we know as library automation. Library automation is the use of automatic and semi-automatic data processing machines to maximize daily activities in the library, such as procurement, processing and circulation or services.
In library circulation service activities, library automation using RFID is widely used to borrow books from the library. Because in addition to student/lecturer cards, one of the applications of ICT is the use of RFID in all books in the college library. That way, the data of all books in the library can be connected and managed with ICT so that it can be used for circulation service activities in the library.
By using RFID in books in the library, librarians only need to put the books to be borrowed on the RFID reader (book reader), the RFID reader will read the tag ID books, check on the library database, then display the book data on the computer screen. If the library user agrees to borrow the book, the system will change the status of the book in the library database as a borrowed book on behalf of the student/lecturer ID. Then the RFID reader will disable the security block on the RFID tag in the book. So if the book was taken out of the library it wouldn’t sound a security alarm. The borrowing process as above has been automated. So students or lecturer who will borrow the book, just put the card on a card reader and a book on book reader at a machine named “auto-borrow”. The machine will then display the borrower data, including name, and the quota of books that can be borrowed, and also displays the books data. Then the borrower simply press the submit button, and the book status change to “borrowed”. This auto-borrow machine is a normal PC connected to a card reader device. In the XYZ library there are 3 units of auto-borrow machines.
The process of borrowing books with an auto-borrow machine helps librarians, so that students, lecturers and staffs can perform self-service in the borrow books. However, the increase in the number of students and lecturers per day, as well as the increase in the number of books borrowed in a day, sometimes created queues on circulation officer and the book “auto-borrow” system.
Therefore, another system that has a similar function to the book auto-borrow system is needed but easy to implement. So, this will help students and lecturers who will borrow book.
 Figure 1: RFID System Phases in Libraries [1]
Figure 1: RFID System Phases in Libraries [1]
2. Objectives and Benefits
XYZ Library has an average of more than 1000 library visitors every year. Library users usually study in the library, read books, looking for journals or periodical, borrow/return books, and so on.
With the current number of smart phones that have been supported by NFC technology, smart phones can be made an application that can be used as an “auto-borrow” device. So students and lecturers who have smart phones with NFC and install the application on their smartphones, can borrow library collections books through their smartphones by attaching the NFC smartphone to the book tag ID, so the book data can be displayed on the smartphone screen.
The objectives of this research are facilitating librarian to collect data for book collection utilities, facilitate user to borrow library collection independently, reducing queues both in circulation staff and auto borrowing machines when borrowing traffic is high in certain times such as before library closes, and as back up systems when auto borrow machine is interrupted or less circulation staff available.
The benefit of this research is identifying and design systems that can optimize the use of RFID with NFC on smartphones in libraries, increase the efficiency and effectiveness of the collection borrowing process in the library, reducing dependence on a collection borrowing process, increasing the efficiency of the library collection procurement budget, and for evaluating library collections utilizations.
Limitation of this research is about systems to optimized use of RFID for auto borrowing library book collection by utilizing NFC Technology on Smartphone at XYZ Library.
Thus, library users who have smartphones with NFC and want to borrow book have another options besides queue at circulation desks or “auto-borrow” machines.
3. Literature Review
Libraries are institutions that manage collections of written works, printed works, and/or recorded works in a professional manner with a standard system to meet the needs of education, research, preservation, information, and recreation of visitors. The law states that the purpose of the library is to provide services to users [2]. Furthermore, these services are described in Article 14, including: library services are carried out in a prime and oriented towards the interests of visitors, and each library needs to develop library services in accordance with advances in information and communication technology. One type of service in the library is circulation services. Circulation services are user services related to borrowing, returning, and extending collections [3].
3.1. Library automation
Library automation is a general term for Information and Communication Technology (ICT) which is used to replace the existing manual systems in libraries. Library automation refers to the use of computers and other peripheral media, such as magnetic media, hard disks, optical media, and so on, as well as the use of computers in accordance with library products and services in displaying all library functions and activities [4].
Below are the advantages of library automation [5]:
- Libraries get ICT infrastructure to support automation
- Optimizing time in doing work
- Avoid duplication of data
- Speed up access to information
- Technology used in library automation provides new learning for librarians.
3.2. RFID
RFID or Radio Frequency Identification is a generic term used to describe a system that transmits the identity (in the form of a unique serial number) of an object or person wirelessly, using radio waves [6]. RFID is usually used for identification and tracking [5].
Auto-ID technologies include bar codes, biometrics, smart cards, voice recognition, and RFID [7]. Auto-ID technology has been used to reduce the amount of time and labor required to manually enter the data, and to improve the accuracy of the data.
There are several components required to use an RFID system:
3.2.1. RFID Tag / RFID Transponder
Tag is a small radio device which is also known as a transponder, smart tags, smart labels, or radio barcode. The tag consists of a simple silicon microchip (usually less than half a millimeter in size) attached aerial and mounted on a substrate [8]. In addition, each tag has a unique ID
The RFID tag contain of at least 2 parts. One is an integrated circuit (chip) for storing and processing information, modulating and demodulating radio frequency (RF) signal, and other specialized functions. The other part is an antenna for receiving and transmitting signals.
This antenna that allows this tag is read by the contactless reader. The larger the antenna can be greater the distance the reader and tag. While chip is for storing the ID number and other information. This chip can be read-only (cannot write other information on this tag), read-write (tags can be read write many times) or write-once read-many (tags can only be written once, but can be repeatedly) [9].
RFID tags have various forms according to needs. For example, the tag for a book is a square form size 5x5cm. For CD/VCD can use round tags that can be embedded in the middle of the CD/VCD. To tack on VHS tapes, RFID tags can be rectangular. In addition, there are also special tags such as tags for tracking fruits, tags that can be implanted under the skin and others.
3.2.2. ISO / IEC 15693 and ISO / IEC 14443g
So that RFID tags can be read by a tag reader from various vendors, RFID tags must have a standard that is used by the RFID reader to be able to communicate using the tag. There are 3 different standards for classifying RFID contactless smart cards [10].
Table 1: Standard contactless smart card
| Standard | Card type | Approximate range |
| ISO/EIC 10536 | Close-coupling | 0-1cm |
| ISO/EIC 14443 | Proximity-coupling | 0-10cm |
| ISO/EIC 15693 | Vicinity-coupling | 0-1cm |
The RFID standard used by library books is ISO 15693, and RFID standard for student and lecturer ID cards uses ISO 14443. Here is a diagram of a standard smart cards, including the contact and contactless [11]
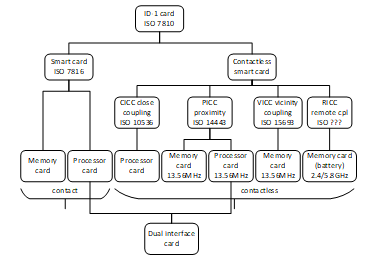 Figure 2: Family of contact and contactless smart card
Figure 2: Family of contact and contactless smart card
3.2.3. Electronic Article Surveillance (EAS)
In a transponder/tag the ID contains a few bytes of data capacity up to several kilo bytes. But, there’s 1 bit in special transponders used for security. One bit of data can provide status on the tag reader: ‘transponder in the field’ or ‘transponders not in the field’.
One transponder bit is used in Electronic Article Surveillance (EAS) to check the status of goods. If the user brings goods / books through the EAS gate with the status ‘transponders in the field’, it will activate an alarm at the EAS gate [11]. Vice versa, if the tag status is ‘transponders not in the field’, the RFID tag will not activate the alarm.
3.2.4. Tag Reader
In addition to tags are also need a tool that serves to read the tags. This tool is called a tag reader. Readers are transceivers (a combination of transmitters and receivers) whose role is to give commands to tags and receive data stored in tags [12]. Because this reader can read the unique ID contained in each tag.
Like tags, readers also have an antenna. Through this antenna, the reader can communicate with the tag. When the reader transmits radio waves, all tags within the transmission area and has the same frequency as the reader, will respond.
Communication between tag readers is done through 3 processes. First, the tag reader is activated by the tag reader radio frequency with 13.56MHz. Once active, the tag will wait for commands from the tag reader. Then, the reader will give commands to the tag and wait for the response from the tag. If the tag receives the valid command, then the tag will respond from the reader command earlier and sent back to the reader. All data transmissions are done through frequency 13.56 MHz [13].
Thus, communication between the reader and tag does not require physical contact (contactless), it can even pass, such as paper, wood, and so on [8].
3.2.5. Near-Field Communication (NFC)
At first, the NFC is not an RFID system, but the interface between the wireless data device, like the infrared or Bluetooth. However, NFC has some interesting characteristics in relation to RFID systems [14].
Data communication between 2 NFC interfaces using 13.56 MHz frequency. Because the same frequency used by the frequency of ISO 15693 and ISO 14443, the devices that support NFC can be used to read the tag ID. NFC is designed to be a secure form of data exchange. NFC device can be an NFC reader or NFC tag. This unique character allows communication between NFC devices [15]. Many smartphones sold in the market today have NFC interfaces. So with a particular application, the smartphone can read the tag ID ISO 15693.
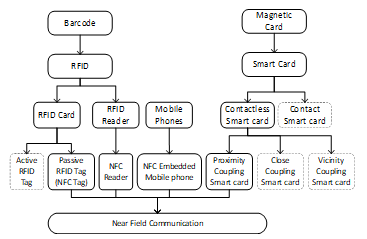 Figure 3: NFC Technology Evolution [16]
Figure 3: NFC Technology Evolution [16]
NFC has 3 communication models [15]:
1.Peer-to-peer
NFC can be used to exchange data between devices, with data exchange rates of up to 424Kbps. It works on the NFCIP-1 protocol, whose details and electromagnetic properties are standardized to ISO 18092 and ECMA 320/440.
2.Reader-writer
NFC can be used to read / write (reader / writer) on tags and smart cards (smart cards). In this communication model, active NFC devices can act as initiators and passive tags act as targets. This mode allows data exchange rates of up to 106 Kbps.
3.Card emulation
In this mode the HFC-handset behaves as a standard smart card. In this mode, the NFC device emulates an ISO 14443 smart card chip. This smart chip is integrated into the mobile device and connected to the NFC module to allow communication to take place [15].
There are several benefits of NFC nowadays. Apart of facilitating cashless and easy payment, NFC can be used for access control, consumer electronic product, health world, facilities for collection and exchange information, coupon and loyalty, and transportation [17]
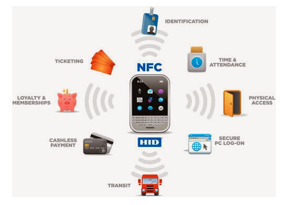 Figure 4: Utilizing NFC in several devices.
Figure 4: Utilizing NFC in several devices.
4. Research Methods
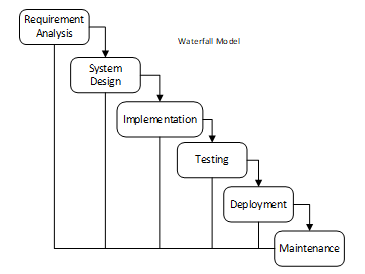
SDLC is the stages of work carried out by system analysts and programmers in building information systems and methods for developing these systems. The system built using SDLC will make it easier to identify problems and design the system as needed in solving these problems. One of the most frequently used SDLC in system development is SDLC Waterfall.
The SDLC Waterfall model is a software development method where the work must be carried out sequentially, each development progress is considered to flow downward, like a waterfall, through several stages that must be carried out. So that software development can be done successfully. In this waterfall model, all phases or stages must be carried out sequentially and until finished, before moving on to the next stage. So, in the waterfall model, each phase can be repeated several times until the phase is completely finished [18]. Researchers are expected to focus on one phase until completion and not work on other phases in parallel [19].
5. Results and Discussion
5.1. Library Database
With the implementation of the RFID system in the library, all the books must be affixed with RFID labels. Tag ID on the label associated with the data in the library books database. Here’s an example in the table below:
Table 2: Example of book database
| Book_tag_ID | Book_id | Book title |
| fef2d68f | 20200200449 | Accounting 1 |
| fef37414 | 19991000919 | Computer Network |
| fef57f30 | 20090100182 | Database Systems |
| … | … | … |
Therefore, if the book is placed/attached to the book reader (RFID reader) on the auto-borrow machine, on an NFC device, as well as in librarian computer, the system will search for the ID tag in the database and will display on screen the data the book data.
Like the book database, the users (lecturers/ students/employees) XYZ University database is also connected with their ID card.
Table 3: Example Univ. XYZ Identity cards database
| Card_tag_id | User_id | Name |
| b0ffc9da | 0210335632 | Anthony |
| 1b9d52ac | 0331970112 | Brown |
| 6385f8f4 | 0123502865 | Charley |
| … | … | … |
After borrowing the book, the user_id, book_id, and date of borrowing will be entered into a book borrowing transaction table. After the book is returned, the table will be updated with the book return date, as in the example below:
Table 4: Example Univ. XYZ Book transaction database
| Book_id | User_id | Borrow_date | Return_date |
| fef2d68f | 0210335632 | 05/20/2020 14:14 | 05/30/2020 10:10 |
| fef37414 | 0331970112 | 07/07/2020 12:13 | 07/14/2020 09:09 |
| fef57f30 | 0123502865 | 11/11/2020 11:11 | NULL |
| … | … | … | … |
5.2. Borrowing Process
For borrowing process using NFC smartphone is similar to borrowing using auto-borrow machine. At the auto-borrow machine, when the user who would like to borrow a book should put a membership card in the card reader and the book to be borrowed in the book reader. To borrow a book with the NFC smartphones, the user must first install the application which will be used for borrowing books. Then users should do the following steps:
- Login to the application using their university email and password.
- Once logged in, then the user can look their borrowing history, check borrowing status, check obligation or can scan a book with RFID tags that will be borrowed by the NFC smartphones.
- The application will look for the data to the library book database server (Table 2) about that book data and display it on the smartphone screen.
- User should click Borrow button if they are sure going to borrow a book.
- The application will update the book transaction database (Table 4) about borrowing the book.
- In addition, the application will tell the NFC device (smartphone) to disable security on the RFID tag a book, so that the book did not make the alarm sounds when taken out of the library area.
6. Use Case
Application use case in NFC smartphones can be described by using use case diagrams as in the picture below :
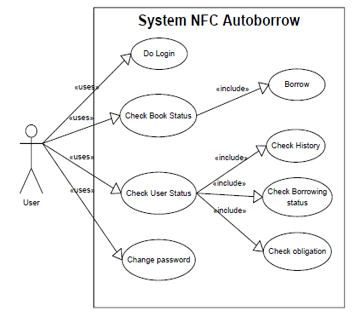 Figure 6: Use case business process NFC auto-borrow system
Figure 6: Use case business process NFC auto-borrow system
After the user (student/lecturer/employee) install an auto-borrow NFC application on a smartphone (which supports NFC), respectively, then the user have to login.
After logging in, users can attach their smartphone to the book to be borrowed. When the book ID tag is detected by the NFC smartphone, the application will search for the book data on the database server according to the ID tag that was read. Book data such as title, author, book code, edition, publisher, year published, and ISBN will display on the smartphone screen. If users want to borrow book, they only need to press the “submit” button. The application will update the book status in the database and disable the EAS (security) status on the book tag.
In addition to lending library books, this application can also be used to view the status of the user. Check history is used to see a list of books that have been borrowed by the user. Check Borrowing Status, useful for checking the current status of borrowed books, including title, author, and book returns due. Check Obligation is useful for viewing user obligations, such as the amount of fines to be paid for late returning the book.
7. Conclusion
From the results of research on the use of NFC on smartphones applied to automatic borrowing (auto-borrow) books in library, it can be concluded as follows:
- Students, lecturers, and employees who have smartphones with NFC can use it to borrow books by them self, no need to queue for the library circulation staff or on auto-borrow computers to borrow books from the library.
- With the NFC’s smartphone capability to deactivate the EAS tag ID (security), it will trigger the programmer to create an application that can be used to disable EAS, and it is certainly influential in terms of the number of lost library books. Because if the EAS is not active, the book will easily be taken out of the library without turning on the alarm system.
8. Recommendations for further research
Application of systems that optimized use of RFID in XYZ library in doing auto borrowing book with utilization of NFC on Smart phone could be used not only for book collection on library but also on other kind of collection that using RFID as security systems. In XYZ library other collection that use RFID are periodical, final works and multimedia collection. Therefor further research, we will measure further optimization for this system for different rules of borrowing library material other than book. Also, its implication on collecting utilization data library collection that only can be read on the spot for library user.
- LibBest, Four phases of library RFID system, Mar. 2020.
- Perpusnas, Undang-undang nomor 43 tahun 2009 tentang perpustakaan, 2009.
- M. Sulaiman, Kepuasan pengguna terhadap fasilitas Auto-Borrowing Machine di Library and Knowledge Center (LKC) Binus University Kampus Anggrek, Universitas Indonesia, 2013.
- A.S. Mishra, T.S. Kumar, “Library automation: issues, challenge, and remedies,” Times International Journal of Research, 9–16, 2015.
- D.M. Pandya, M. Darbar, “Benefits and disadvantage of library automation: a study of academic library users,” International Journal of All Research Education and Scientific Methods (IJARESM), 14–19, 2017.
- M. Roberti, RFID journal, Emerald X, 2020.
- What is automatic identification (auto-id), IGI Global, 2013.
- RFID technology, RFID Centre, May 2020.
- V.D. Hunt, A. Puglia, M. Puglia, RFID – A Guide to Radio Frequency Identification, John Wiley & Sons, Inc., New Jersey, 2006, doi:10.1002/0470112255.
- M. Zurita, R.C.S. Freire, S. Tedjini, S.A. Moshkalev, “A Review of Implementing ADC in RFID Sensor,” Journal of Sensors, 1–14, 2016, doi:10.1155/2016/8952947.
- K. Finkenzeller, RFID Handbook, John Wiley & Sons, Ltd, West Sussex, UK, 2010, doi:10.1002/9780470665121.
- N.K. Singh, P. Mahajan, “Application of RFID technology in libraries,” International Journal of Library and Information Studies, 1–9, 2014.
- J. Scalzo, J. Gates, V. Potnis, M. Howell, W. Tran, Using ISO 15693 compliant RFID tags in an inventory control system, Louisiana.
- C.-H. Lin, P.-H. Ho, H.-C. Lin, “Framework for NFC-Based Intelligent Agents: A Context-Awareness Enabler for Social Internet of Things,” International Journal of Distributed Sensor Networks, 10(2), 978951, 2014, doi:10.1155/2014/978951.
- D. Trivedi, “Near field communication,” Institute Of Technology Nirma University, Ahmedabad, 2015.
- V. Coskun, K. Ok, B. Ozdenizci, Near field communication: from theory to practice, John Wiley & Sons, Ltd., West Sussex, UK, 2012.
- M. Rifqi, N.K. Wardhani, “Aplikasi peran dan kegunaan teknologi near field communication (NFC) terhadap kegiatan proses belajar mengajar di perguruan tinggi (studi kasus: Universitas Mercu Buana),” Jurnal Ilmu Teknik Dan Komputer, 1(1), 20–26, 2017.
- Y. Bassil, “A simulation model for the waterfall,” International Journal of Engineering & Technology (IJET), 2012.
- W. Nugraha, M. Syarif, W.S. Dharmawan, “Penerapan metode SDLC waterfall dalam sistem informasi inventory barang berbasis desktop,” JUSIM (Jurnal Sistem Informasi Musirawas), 3(1), 22–28, 2018, doi:10.32767/jusim.v3i1.246.